Introduction
New Remote Code Execution (RCE) vulnerabilities were announced in Spring Framework, which is a lightweight open-source application framework that provides a comprehensive programming and configuration model for modern Java-based enterprise applications. Spring is commonly known as one of the most popular Java frameworks, where Java programming language is widely used for web system development.
The Spring Cloud Expression Resource Access (CVE-2022-22963) was first tracked on Mar 29, 2022, which allowed for an injection of specially crafted SpEL as a routing expression that may result in remote code execution and access to local resources. Two days later, the vulnerability called Spring Framework RCE via Data Binding on JDK 9+ (CVE-2022-22965), also known as SpringShell (and/or Spring4Shell), whose severity is critical, is patched by the Spring Framework. If exploited, A Spring MVC or Spring WebFlux application running on JDK 9+ may be leveraged by attackers via this vulnerability to perform remote code execution (RCE).
Affected Version
For Spring Framework 5.3 branch, version earlier than 5.3.18
For Spring Framework 5.2 branch, version earlier than 5.2.20
Defense and Fix Suggestions
It is suggested that the affected 5.2.x users should upgrade to 5.2.20+ and the affected 5.3.x users should upgrade to 5.3.18 for mitigation.
Hillstone Networks also released IPS signature database 2.1.451 for the NGFW products, IPS signature database 3.0.102 for the NIPS and sBDS products, and WAF signature database version 1.1.138 for the WAF and sBDS products.
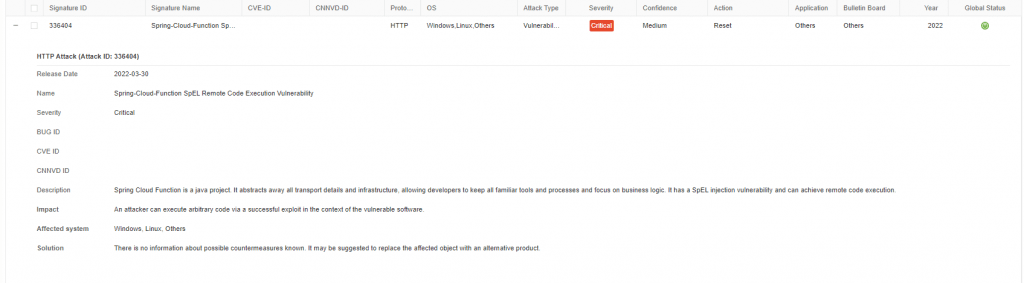
Figure 1. Screenshot of IPS signature for Spring4Shell vulnerability
Customers of Hillstone Networks is recommended to upgrade the signature database to receive protection.



