Integrative Cybersecurity
Visionary. AI-powered. Accessible.
BRINGING CYBERSECURITY CHALLENGES
Digital Transformation
Digital transformation is a priority for every company and a challenge for every IT organization, as data drives the business, and data is now generated, processed, and analyzed everywhere—in the data center, on the edge, in one or multiple clouds. Digital transformation brings three critical challenges for CISOs:

Rapidly Evolving Infrastructure
In today’s digitally transformed landscape, data centers have evolved beyond traditional on-premises confines, extending into the realms of cloud computing and edge devices. Combined with work-from-anywhere adoption, the result is a target-rich environment where hackers and nefarious actors now have an expansive attack surface and corresponding attack vectors.
Fast Changing Threat Landscape
The expansive attack surface has become a goldmine and multi-stage, multi-layer attacks occur daily. Attackers are becoming more skilled and creative in their methods by using the same cutting-edge AI/ML tools to hone their art and deliver more sophisticated attacks. Ransomware, supply chain attacks, and zero-day vulnerabilities remain significant areas of concern.
Increasing Complexity and Cost
Multifold increases in attack surfaces, frequency, and variety of attacks, along with complex network topology and deployment, are not necessarily matched by corresponding budget growth for security initiatives. Skill gaps are ubiquitous. CISOs are under pressure to provide increased protection while seeking available and qualified personnel and holding firms to a budget line.
The Hillstone Approach
Integrative Cybersecurity
Integrative Cybersecurity
Hillstone’s Integrative Cybersecurity eliminates gaps in protection that put your enterprise at risk and reduces layers of complexity and cost, from technology to solutions, to their delivery and functionality, across vendors and platforms. Hillstone’s Integrative Cybersecurity solutions bring coverage, control, and consolidation to secure the digital transformation at global scale:
What is Integrative Cybersecurity?
Coverage, Control and Consolidation are the core tenets of an integrative cybersecurity solution.
Coverage – The mandate of the modern enterprise is to utilize the technology and infrastructure needed to grow and thrive. From containers to clouds and servers to SaaS, an integrative cybersecurity strategy provides adaptive protection for any environment, ensuring resilience against evolving threats.
Control – Maintaining the security and performance of enterprise technology is an exhausting balancing act. The right solution for the business isn’t always the most recent or most-popular version, but it always needs to be secure. An integrative cybersecurity approach is adaptive and puts the enterprise in control.
Consolidation – Complex environments have attack surfaces that sprawl and edges that evaporate. Mitigating every attack vector with individual solutions creates opaque and siloed security operations that are both porous and inefficient. An integrative cybersecurity approach reduces complexity through consolidation.
What We Do
A Three-Pronged Methodology
Hillstone’s Integrative Cybersecurity solution is a seamless blend of data, analysis, and defense that’s both proactive and intelligent. It delivers depth and breadth of protection to companies of all sizes, from edge to cloud, across any workload to:
Secure the Networks: Zero Trust starts here.
Hillstone’s Future-ready Network Security provides a scalable security architecture for growing infrastructures and business expansion. It lays the groundwork for a zero-trust architecture that supports emerging technologies and combats sophisticated cyber threats. Hillstone’s next-generation A-Series and X-Series firewalls ensure high-performance and dependable network protection, with advanced threat detection and prevention to safeguard digital assets for enterprises and service providers.

Secure the Networks: Zero Trust starts here.
Hillstone’s Future-ready Network Security provides a scalable security architecture for growing infrastructures and business expansion. It lays the groundwork for a zero-trust architecture that supports emerging technologies and combats sophisticated cyber threats. Hillstone’s next-generation A-Series and X-Series firewalls ensure high-performance and dependable network protection, with advanced threat detection and prevention to safeguard digital assets for enterprises and service providers.
Mitigate the Threats: Before they attack you.
Cyber threats like ransomware, supply chain attacks, and zero-day vulnerabilities are inevitable, constantly evolving in complexity. These threats can remain undetected while compromising data. Hillstone’s AI-powered Threat Detection and Response proactively identifies and neutralizes such attacks, protecting critical data assets. Utilizing advanced machine learning, Hillstone’s NDR and XDR solutions detect and analyze anomalies and correlations to prevent and mitigate threats automatically.

Mitigate the Threats: Before they attack you.
Cyber threats like ransomware, supply chain attacks, and zero-day vulnerabilities are inevitable, constantly evolving in complexity. These threats can remain undetected while compromising data. Hillstone’s AI-powered Threat Detection and Response proactively identifies and neutralizes such attacks, protecting critical data assets. Utilizing advanced machine learning, Hillstone’s NDR and XDR solutions detect and analyze anomalies and correlations to prevent and mitigate threats automatically.
Protect the workloads: Wherever they run.
In an era of digital transformation, businesses use a mix of legacy and cloud-native applications, creating security challenges for IT as workloads and data are vulnerable across various environments. Hillstone’s Uncompromising Cloud Workload Protection, through CloudArmour CWPP and CloudHive Micro-segmentation solutions, ensures robust security for an enterprise’s virtualized and cloud-native workloads, safeguarding them without compromise.

Protect the workloads: Wherever they run.
In an era of digital transformation, businesses use a mix of legacy and cloud-native applications, creating security challenges for IT as workloads and data are vulnerable across various environments. Hillstone’s Uncompromising Cloud Workload Protection, through CloudArmour CWPP and CloudHive Micro-segmentation solutions, ensures robust security for an enterprise’s virtualized and cloud-native workloads, safeguarding them without compromise.
Advanced Products
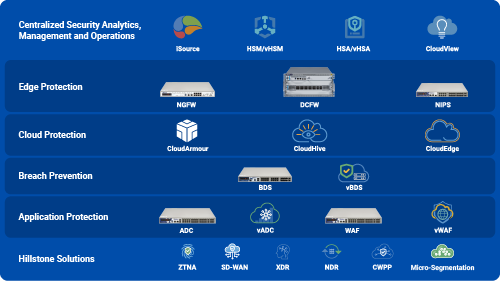
Integrative Cybersecurity Solutions for Global Enterprises
The Hillstone Networks suite of products can help establish a comprehensive security infrastructure. We have edge protection, cloud protection, server protection, application protection, and a set of centralized security analytics that can help with streamlining overall security management and operations.
Hillstone’s Innovation Advantages

Visionary.
Hillstone has Continuously pushed the boundaries of innovation with visionary cutting-edge technologies from day one, making it a visionary in Gartner Magic Quadrant for Network firewalls and also named a leader in Frost & Sullivan Next Generation Firewall Radar and XDR Radar.
AI-powered.
Having pioneered AI/ML technology in cyber security with the first AI-powered firewall in 2014, Hillstone leverages its established expertise in AI/ML with continuous innovation extending to newer products such as the advanced NDR and XDR platforms.
Accessibile.
Hillstone’s cybersecurity solutions cater to both large enterprises and SMBs, designed to reduce the total cost of ownership with an unparalleled licensing model and price-to-performance ratio.
CONTACT US
Ready to chat with our experts?
CONTACT US
Ready to chat with our experts?
Like what you see? Looking for a deeper understanding? Or simply, looking to act and secure your enterprise today? Let us know how we can help you and we will connect you to the right person as soon as possible.
Contact request
Fields marked with an asterisk are required.