Introduction
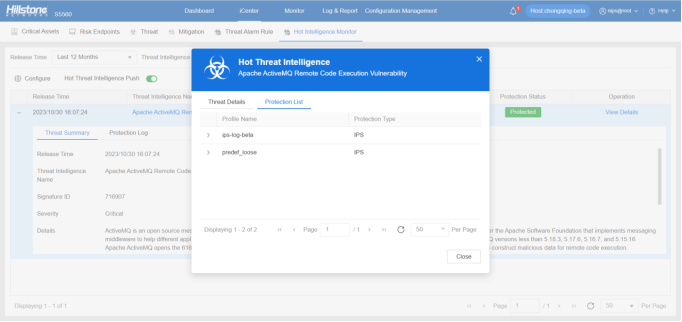
Apache ActiveMQ, a prominent open-source message broker and integration pattern server, facilitates communication between diverse applications or systems using the Java Message Service (JMS) API. It has recently come under scrutiny due to a critical vulnerability that lies in the improper handling of data on the 61616 service port during default installations, opening a gateway for potential remote code execution attacks.
Vulnerability
The CVE-2023-46604 Apache ActiveMQ vulnerability stems from a failure to adequately filter incoming data on the 61616 service port. In default configurations, this port lacks proper validation mechanisms, enabling attackers to craft malicious data packets with the intent of executing arbitrary code on the targeted system. Remote code execution vulnerabilities are particularly perilous as they grant unauthorized access and control over the affected system, allowing attackers to execute commands, exfiltrate sensitive data, or even compromise the entire infrastructure.
Attackers exploiting this vulnerability could send specially crafted data packets to the 61616 port, leveraging the absence of proper filtering. Once received, the malicious payload could be executed within the ActiveMQ environment, leading to unauthorized access, data breaches, or even complete system compromise. The ramifications of such an exploit extend beyond mere inconvenience, posing severe threats to the confidentiality, integrity, and availability of the affected systems.
Affected Version
5.18.0 <= Apache ActiveMQ < 5.18.3
5.17.0 <= Apache ActiveMQ < 5.17.6
5.16.0 <= Apache ActiveMQ < 5.16.7
Apache ActiveMQ < 5.15.16
Remediation
Official fix: To address this critical vulnerability, users are recommended to upgrade to version 5.15.16, 5.16.7, 5.17.6, or 5.18.3, which fixes this issue. Please visit: https://activemq.apache.org/components/classic/download/
Implementing the Fix
Upgrade your IPS signature database to version 3.0.180 and your AV signature database to version 2.1.530 to ensure that Hillstone Networks Intrusion Prevention System (NIPS) and Hillstone Breach Detection System (BDS) are equipped to detect and provide protection against this vulnerability.
The hotspot intelligence of this vulnerability is available on Hillstone Networks iSource as well.