VMWare officially issued a security bulletin, disclosing the authentication bypass vulnerability (CVE-2022-22978). The Hillstone sBDS Solution can support the detection of this vulnerability.
Introduction
VMWare officially issued a security bulletin, disclosing the authentication bypass vulnerability (CVE-2022-22978). It exists in specific versions of Spring Security, a security management framework in the Spring family.
Vulnerability
The nature of the regular expression writer RegexRequestMatcher is to allow for flexible configurations, as noted by the dotted symbols (.) representing wildcards. These symbols are useful for writing flexible regular expressions, be it for fuzzy matching purposes, or for more flexible configuration requirements to follow by. However, recently, it was discovered that when using RegexRequestMatcher in Spring Security, regular expressions containing dotted symbols could result in the creation of malicious packets that attackers can leverage to bypass authentication on some servlet containers.
Affected Version
Spring Security 5.5.x < 5.5.7
Spring Security 5.6.x < 5.6.4
Remediation
The vendor has released the patches and we recommend users to update Spring Security 5.5.x to 5.5.7, and Spring Security 5.6.x to 5.6.4. Please visit:
https://github.com/spring-projects/spring-security/releases/tag/5.5.7
https://github.com/spring-projects/spring-security/releases/tag/5.6.4
Preventing attackers from being able to edit their LDAP user entry prevents them from controlling the inputs required to make this attack.
Implementing the Fix
The Hillstone sBDS Solution can support the detection of this vulnerability.
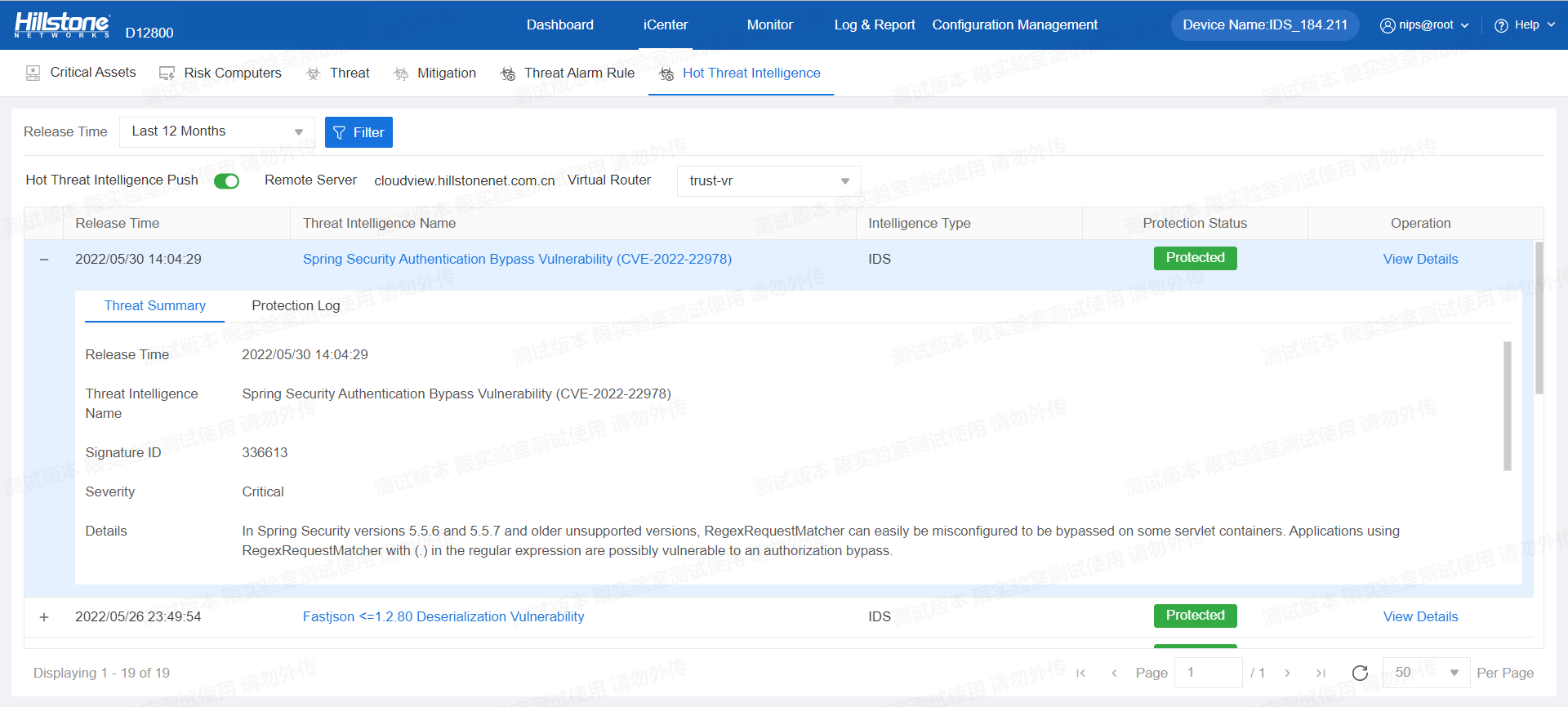
Figure 1. Authentication bypass vulnerability detected by Hillstone IDS
The hotspot intelligence of this vulnerability is available on Hillstone iSource as well.
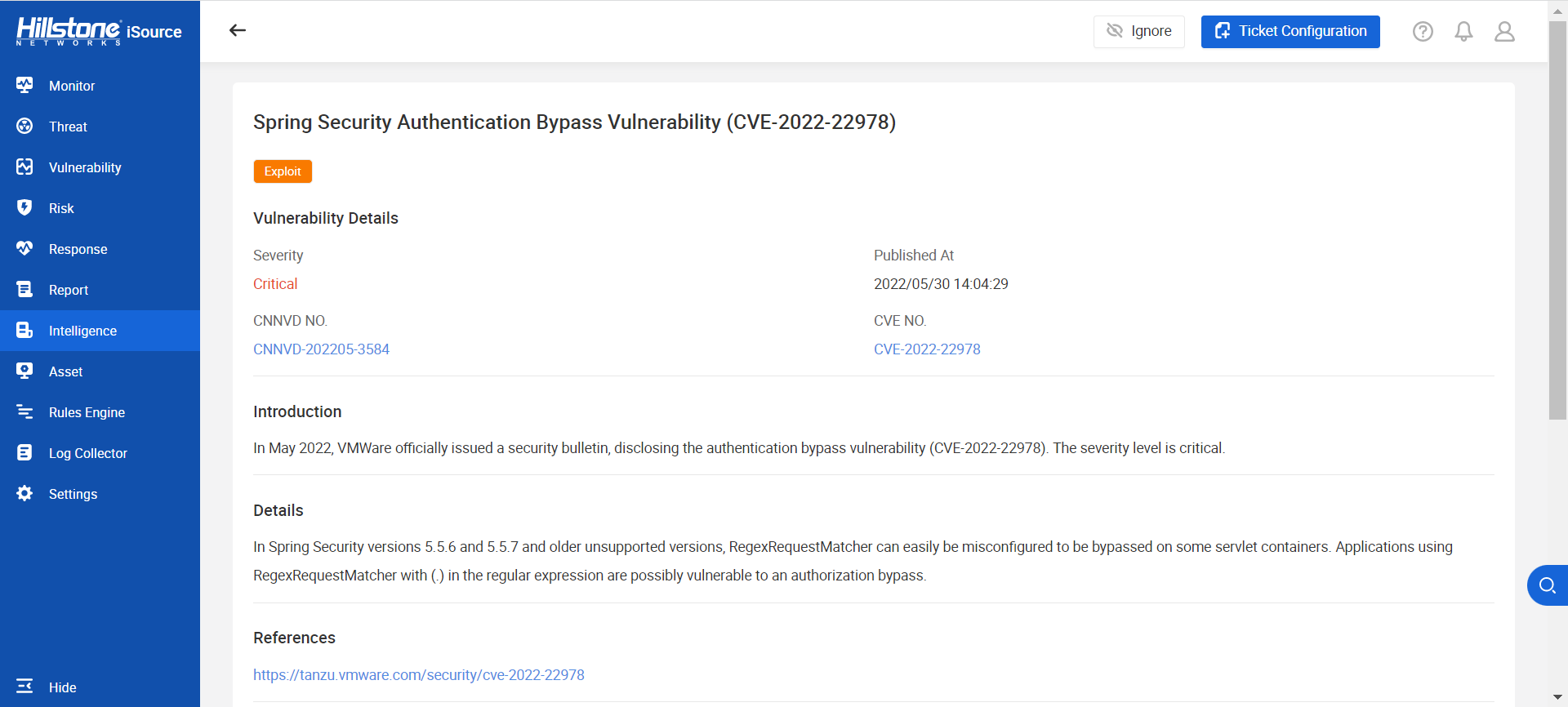
Figure 2. Hotspot intelligence on Hillstone iSource



