[Overview]
Remote Desktop Services (RDS) is one of the components of Microsoft Windows that allow users to remotely access and take control of a computer or virtual machine. Recently, the Remote Desktop Services Remote Code Execution vulnerability was published officially.
[Vulnerability Details]
CVE-2019-0708: The vulnerability is pre-authentication and requires no user interaction. A remote attacker could exploit this vulnerability by connecting to the target system using RDP and sending specially crafted requests. Successful exploitation could cause arbitrary code execution on the target system, as well as data leakage and modification or illegal accounts creation.
Vulnerability Source: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-0708
[Severity]
Critical
[Affected Versions]
- Windows 7
- Windows Server 2008 R2
- Windows Server 2008
- Windows 2003
- Windows XP
[Suggestions]
Update the official fixes to avoid being affected by the vulnerability
For users who cannot install Windows Update and have no security device protection, the following measures can be taken:
1. Disable remote desktop services
2. Block access to the remote desktop TCP port (3389 in default) in the host firewall
3. Enable Network Level Authentication (NLA), which applies to Windows 7, Windows Server 2008, and Windows Server 2008 R2
Official advice: https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0708
[Hillstone Networks Solutions]
Hillstone Networks has added signatures to the IPS signature database version 2.1.292. By deploying any Hillstone Networks solution with the IPS function, Remote Desktop Services Remote Code Execution Vulnerability can be quickly detected and effectively intercepted, preventing the server from being attacked.
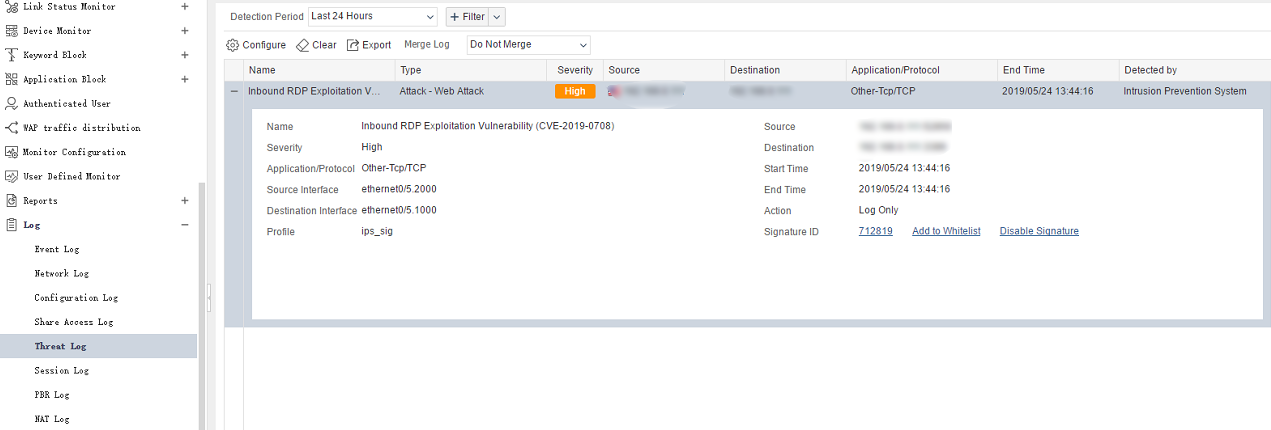
Threat Events Detected by Hillstone Solutions
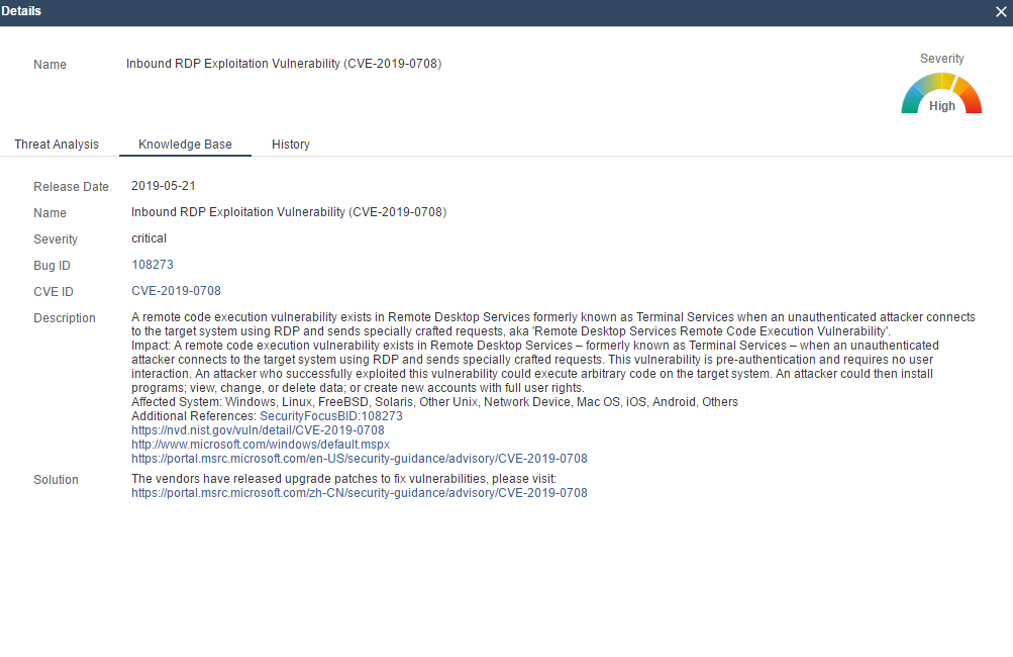
Vulnerability Detail Description


