[Overview]
389 Directory Server is an OpenLDAP-based enterprise LDAP server developed by Red Hat. It is an open source Lightweight Directory Access Protocol (LDAP) service implementation. Red Hat fixes a buffer overflow vulnerability in the latest update.
[Vulnerability Details]
CVE-2018-1089: This vulnerability is caused by the inability to handle excessively long filter values in ldapsearch queries. An unauthenticated attacker could exploit this vulnerability by sending maliciously long filter values in an LDAP search request.
If the vulnerability is successfully exploited, it will lead to arbitrary code execution. If the exploitation is unsuccessful, the ns-slapd program will stop abnormally.
Vulnerability Source: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-1089
[Severity]
Critical
[Affected Versions]
- Red Hat 389 Directory Server prior to 1.3.6.15
- Red Hat 389 Directory Server prior to 1.3.8.1
- Red Hat 389 Directory Server prior to 1.4.0.9
[Suggestions]
Update the bug fix release provided by Redhat to eliminate the damage caused by the vulnerability.
Only trusted, authenticated users are allowed to bind to the server
Official advice: https://access.redhat.com/errata/RHSA-2018:1380
[Hillstone Networks Solutions]
Hillstone Networks has added signatures to the IPS signature database version 2.1.257. By deploying any Hillstone Networks solution with the IPS function, the the Red Hat 389 Directory Server nsslapd ldapsearch Buffer Overflow vulnerability can be quickly detected and effectively intercepted, preventing the server from being attacked.
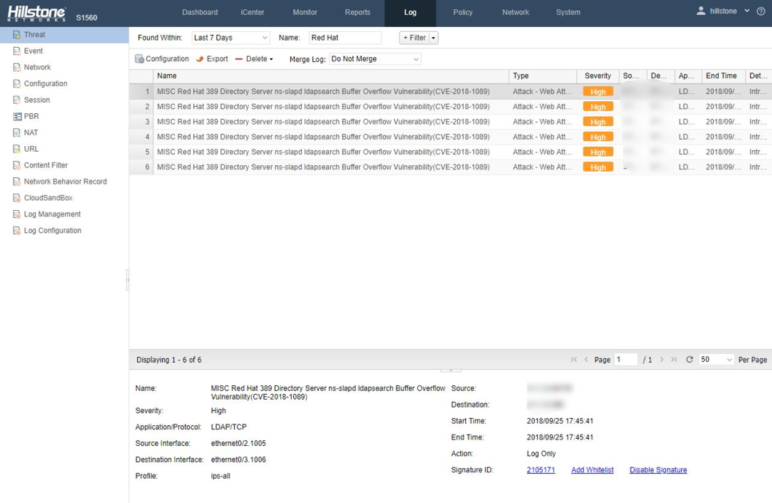
Threat Events Detected by Hillstone Solutions
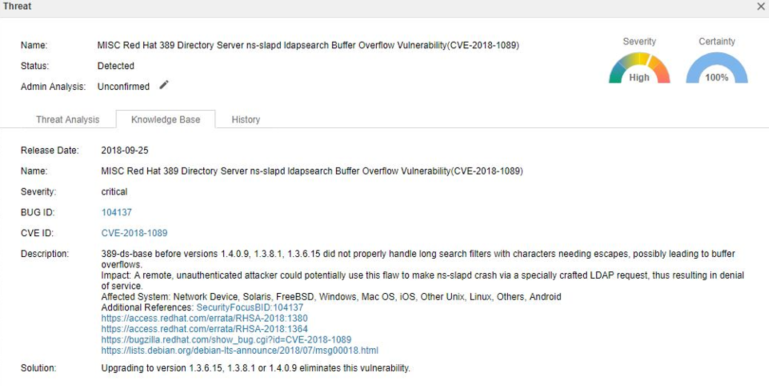
Vulnerability Detail Description


