[Overview]
WebLogic Server is a Java application server platform for developing, integrating, deploying, and managing large distributed web applications, network applications, and database applications. Recently, Oracle released an update patch to fix the WebLogic Server deserialization vulnerability.
[Vulnerability Details]
CVE-2018-3245: The vulnerability is caused by deserializing suspicious data in a T3 protocol request. An unauthorized attacker could exploit this vulnerability by sending a request for a specially crafted UnicastRef object to a vulnerable service.
If the vulnerability is exploited successfully, an outgoing JRMP session from the target server to an attacker controlled server will allow the attacker to respond with malicious serialized objects that cannot be matched by any blacklist, causing Oracle WebLogic Server to be taken over.
Vulnerability Source: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-3245
[Severity]
Critical
[Affected Versions]
- Oracle WebLogic Server 10.3.6.0
- Oracle WebLogic Server 12.1.3.0
- Oracle WebLogic Server 12.2.1.3
- Oracle WebLogic Server prior to Docker 12.2.1.3.20180913
[Suggestions]
Update the bug fix release provided by Oracle to eliminate the damage caused by the vulnerability.
Prevent WebLogic Server from communicating with suspicious network through port 7001
Official advice: https://www.oracle.com/technetwork/security-advisory/cpuoct2018-4428296.html
[Hillstone Networks Solutions]
Hillstone Networks has added signatures to the IPS signature database version 2.1.261. By deploying any Hillstone Networks solution with the IPS function, Oracle WebLogic Server RemoteObject Insecure Deserialization vulnerability can be quickly detected and effectively intercepted, preventing the server from being attacked.
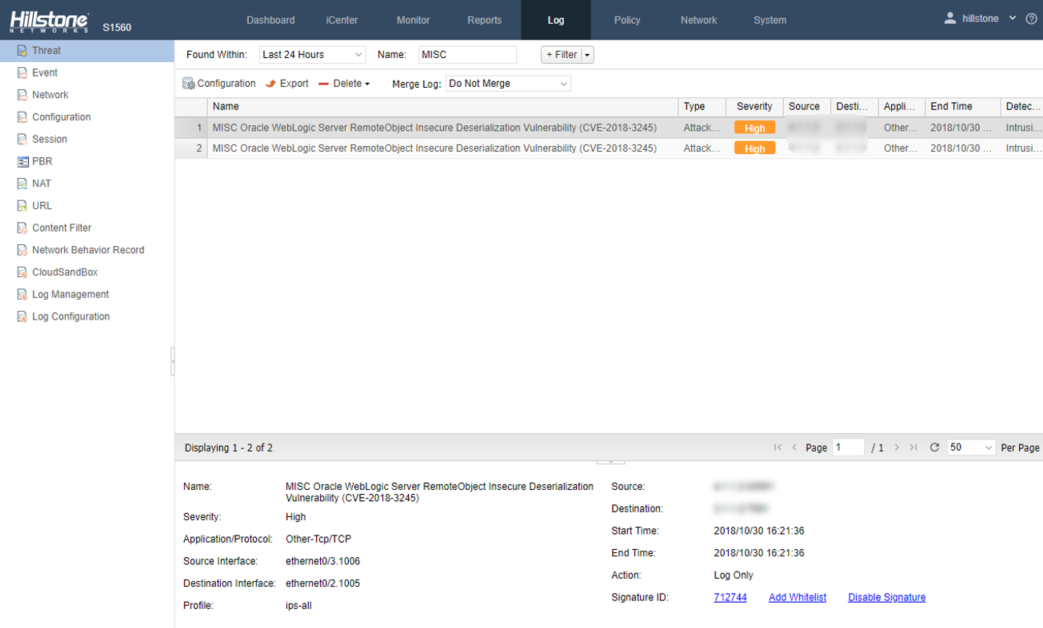
Threat Events Detected by Hillstone Solutions
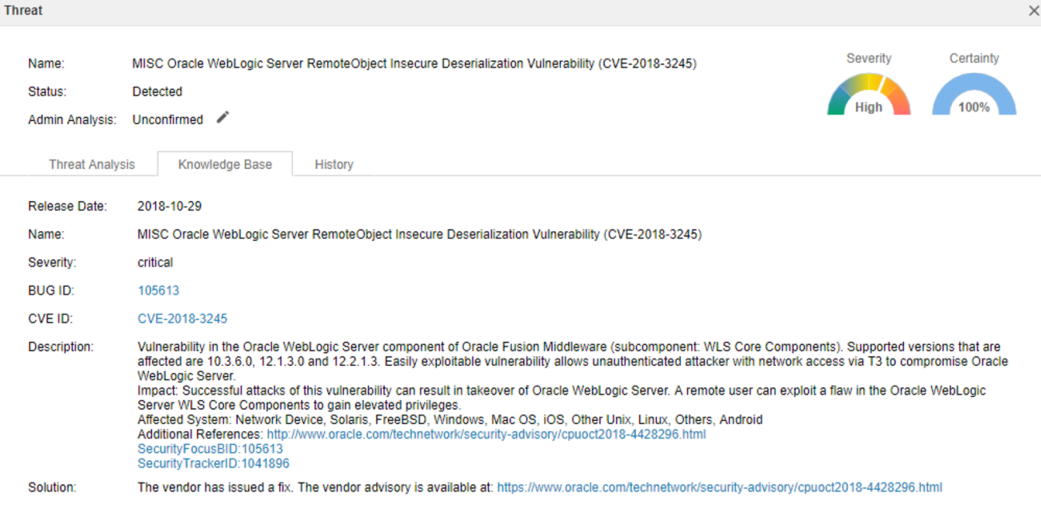
Vulnerability Detail Description


