[Overview]
Microsoft Office is an office software developed by Microsoft Corporation that can perform word processing, form editing, slide show production, and Email service. Recently, Microsoft fixed a remote code execution vulnerability in it.
[Vulnerability Details]
CVE-2018-8161: The vulnerability is caused by Outlook’s incorrect parsing of HTML. The vulnerable condition occurs when a MIME message with a Content-Type specifying HTML content (“text/html”) is parsed by Outlook. Hackers can exploit this vulnerability by sending malicious emails to targeted users.
If the vulnerability is exploited successfully, it will allow the attackers to execute arbitrary codes in application environment.
Vulnerability Source: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-8161
[Severity]
Critical
[Affected Versions]
- Microsoft Office 2010 Service Pack 2
- Microsoft Office 2013 RT Service Pack 1
- Microsoft Office 2013 Service Pack 1
- Microsoft Office 2016
- Microsoft Office 2016 Click-to-Run (C2R)
- Microsoft Office 2016 for Mac
- Microsoft Office Online Server 2016
- Microsoft Office Web Apps 2010 Service Pack 2
- Microsoft Office Web Apps Server 2013 Service Pack 1
[Suggestions]
Update the bug fix release provided by Microsoft to eliminate the damage caused by the vulnerability.
Do not easily click on emails from strangers.
Official advice: https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2018-8161
[Hillstone Networks Solutions]
Hillstone Networks has added signatures to the IPS signature database version 2.1.268. By deploying any Hillstone Networks solution with the IPS function, Microsoft Office Remote Code Execution Vulnerability can be quickly detected and effectively intercepted, preventing the server from being attacked.
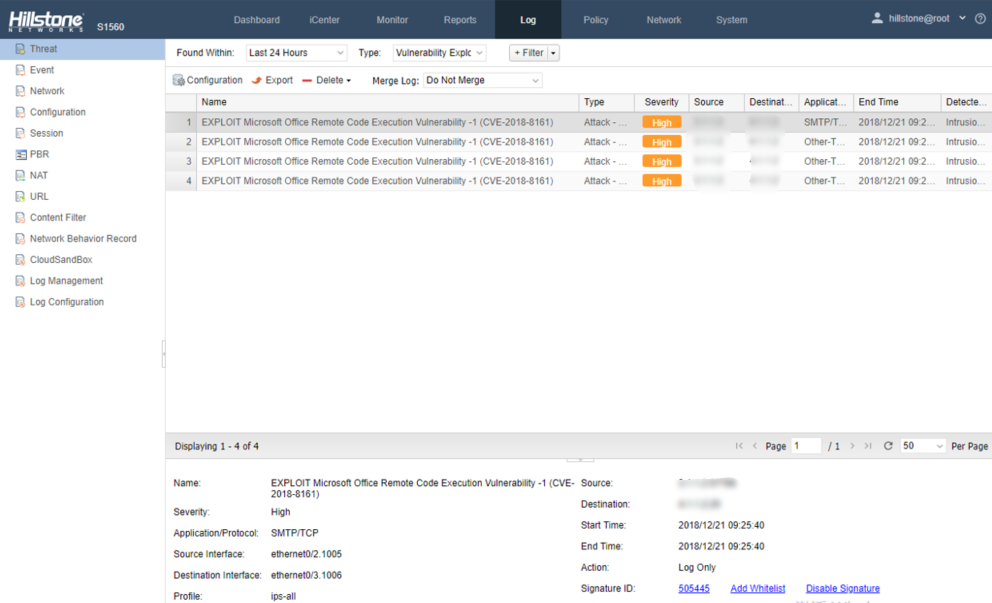
Threat Events Detected by Hillstone Solutions
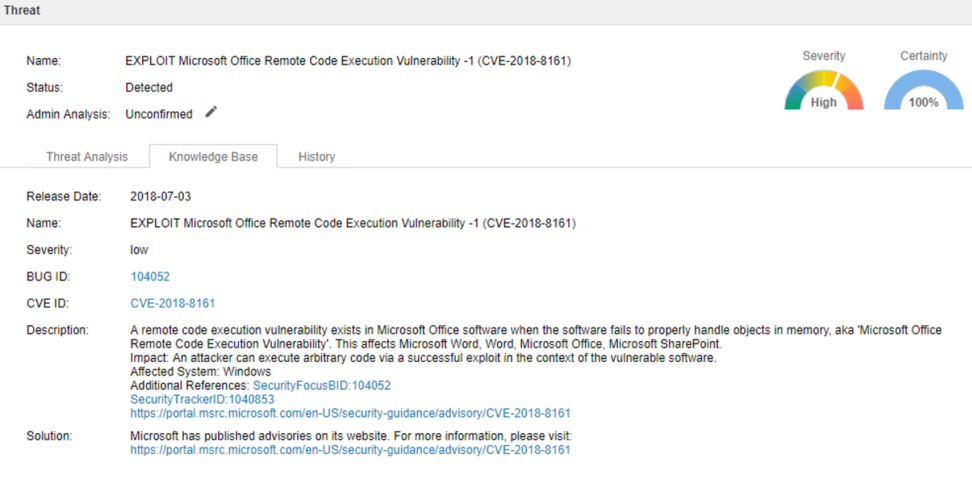
Vulnerability Detail Description


