[Overview]
Apache Tomcat is a free open source web application server. It is a relatively popular web application server, being widely used in the framework of web application services. Recently, a file of Tomcat was found to contain vulnerabilities. At present, a new version has been released for the vulnerability fix. Meanwhile, Hillstone Networks has released signatures against this vulnerability. It is recommended that users patch or upgrade the intrusion detection signature database of network security devices in time for protection.
[Vulnerability Details]
CVE-2020-1938 (CNNVD-202002-1052): An Apache Tomcat file inclusion vulnerability. This vulnerability uses the AJP protocol port (default 8009) to attack. The attacker could exploit this vulnerability by sending constructed data through the AJP protocol defect to read any file in web application directory. If the server has a file upload function, it may cause arbitrary code execution.
Vulnerability Source: https://cve.mitre.org/cgi-bin/cvename.cgi?name=2020-1938
[Severity]
High
[Affected Versions]
- Apache Tomcat 6
- Apache Tomcat 7 < 7.0.100
- Apache Tomcat 8 < 8.5.51
- Apache Tomcat 9 < 9.0.31
[Suggestions]
- Update the official fixes to avoid being affected by the vulnerability
- If it cannot be updated immediately, temporary mitigation measures should be taken:
- If Tomcat AJP protocol is not used, it is recommended to close the AJP connector or change its listening address to only localhost.
- If Tomcat AJP protocol is used, it is recommended to configure requiredSecret for the AJP connector to set the AJP protocol authentication credentials.
- Network security device upgrades intrusion detection signature database.
[Hillstone Networks Solutions]
Hillstone Networks has added this threat behavior to the signature list. Signature Database Version: 2.1.337. By deploying Hillstone Networks NIPS, NGFW, CloudEdge, CloudHive, and sBDS, Apache Tomcat File Inclusion vulnerability can be quickly detected and effectively intercepted, preventing server from being attacked.
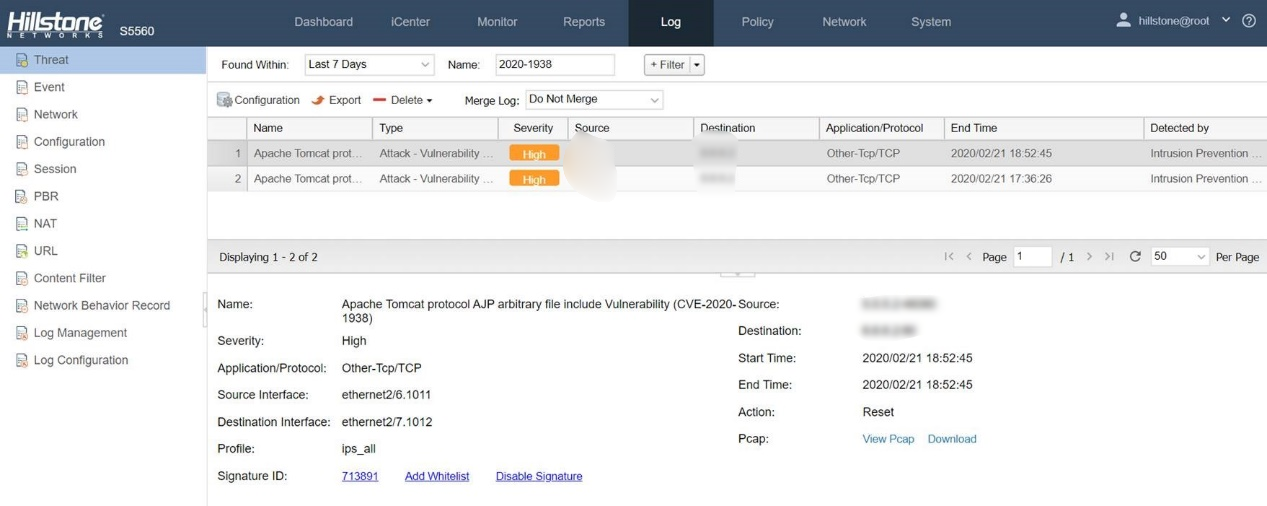
Threat Events Detected by Hillstone Solutions
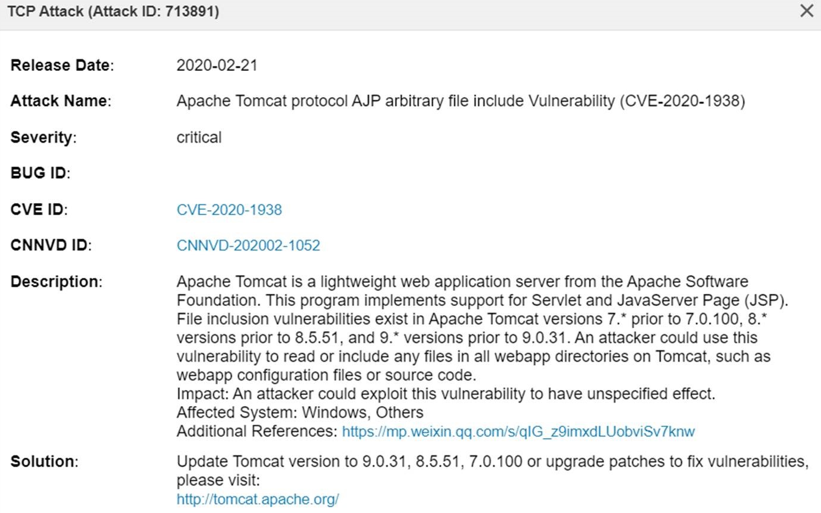
Vulnerability Detail Description


