On March 2, Microsoft released emergency security updates for four Exchange Server vulnerabilities. Exchange server versions ranging from 2013 through 2019 are all affected. Upon successful exploitation, an attacker can steal victim’s emails from Exchange server, as well as install web shells on the servers to gain remote control.
Microsoft also cautioned that the vulnerabilities were actively used in the wild by a hacker group dubbed Hafnium. Details can be found here. The NIST national vulnerability database lists the severity of these vulnerabilities as High, and in one case, CVE-2021-26855, Critical.
Microsoft’s initial advisory about the Exchange flaws credited Volexity, a Virginia based security company, for reporting the vulnerabilities. According to Volexity’s President Steven Adair, the attackers had been exploiting these vulnerabilities since as early as January 3, 2021. The Microsoft advisory suggests that the best protection is to apply updates as soon as possible across all impacted systems.
The details on the Exchange server vulnerabilities are listed below:
This is a server-side request forgery (SSRF) vulnerability in Exchange. It allows an attacker to bypass authentication on a vulnerable Exchange server.
This an insecure deserialization vulnerability in the Unified Messaging service. Successful exploitation of this vulnerability will allow an attacker to run code as SYSTEM on a vulnerable Exchange server.
This is a post-authentication arbitrary file write vulnerability in Exchange. If successfully exploited, an attacker can install a web shell on a vulnerable exchange server.
This is also a post-authentication arbitrary file write vulnerability in Exchange that NIST has identified as unique from the others in this list. If successfully exploited, an attacker can install a web shell on a vulnerable Exchange server.
Patches have been released by Microsoft for all the above CVEs. The list of patches listed below. CUSTOMERS ARE ADVISED TO INSTALL THESE PATCHES IMMEDIATELY.
Patches for Microsoft Exchange vulnerabilities:
- CVE-2021-26855: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26855
- CVE-2021-26857: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26857
- CVE-2021-26858: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-26858
- CVE-2021-27065: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-27065
Hillstone Networks’ threat response team has taken immediate actions to stop the threat for our customers. Hillstone Networks’ updated IPS signatures have been released. Figure 1. Shows Hillstone Networks NIPS defense effect. Admins for the following Hillstone Networks products should update their IPS signature version to 2.1.393.
- Hillstone Networks NIPS
- Hillstone Networks Firewalls
- Hillstone CloudEdge
- Hillstone CloudHive
- Hillstone sBDS
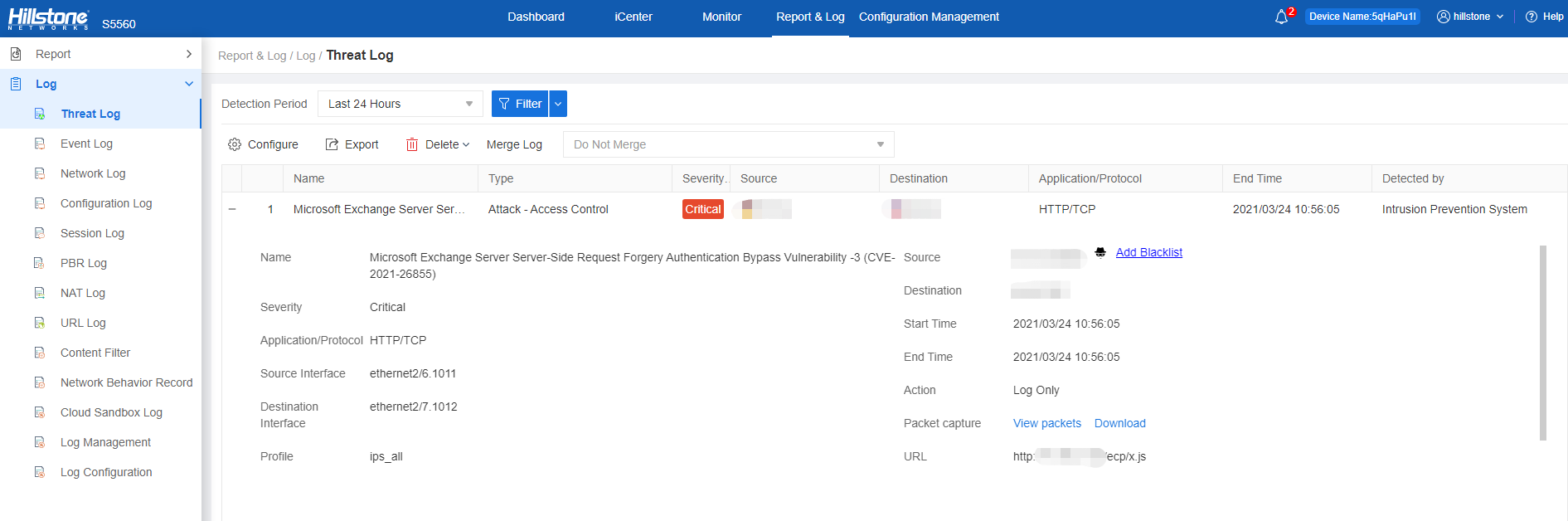
Figure 1: Hillstone Networks NIPS Defense Effect
If you’d like to learn more, please reach out to us. Our friendly and knowledgeable team is happy to help.



