The complexity and diversity of hybrid cloud architectures present special challenges for IT and security teams. The recently released Gartner “Market Guide for Cloud Workload Protection Platforms,2020*” provides valuable guidance for anyone tasked with ensuring the security of these architectures.
In the new market guide, Gartner says, “container and serverless workloads are scanned for vulnerabilities and misconfigurations in development, but are deployed with little or no runtime protection within the workload and instead rely on external network instrumentation and event monitoring to detect threats.”
Gartner acknowledges Hillstone Networks as a representative vendor in the category of “identity-based segmentation and network visibility” through Hillstone’s CloudHive product.
In the report, Gartner states the following regarding network firewalling, visibility and micro-segmentation:
“A key requirement of workload security is firewalling/segmentation of the workload’s ability to communicate with other resources. However, some enterprises don’t need the CWPP offering to perform this function. Instead, they use the built-in segmentation of the cloud infrastructure”
Although Hillstone CloudHive in our opinion, fits within this category, it offers security features far beyond L3 and L4 firewalling and segmentation. First, CloudHive provides a series of auto-discovery functionalities, including VM auto-discovery, application identification, service identification, and service chain discovery. Second, visibility is provided based on the discovered assets, like traffic visibility, service chain visibility and threat visibility.
On top of those features, CloudHive offers network and service performance monitoring. All these features help cloud administrators or tenants gain visibility into cloud east-west traffic, implement segmentation, and monitor performance on network infrastructure and services. These features are not commonly provided by the cloud infrastructure itself.
In addition to firewalling, CloudHive provides a set of NGFW security features, like IPS, Antivirus, URL filtering, etc. The deployment position of the CloudHive Security Service Module allows it to monitor and control inter-VM traffic within the data center. With the rich security features and deployment in close proximity to the VMs, CloudHive is even capable of providing security protections in the layers of “HIPS with vulnerability shielding” and “Anti-malware scanning.” Key security features from CloudHive can be categorized into three layers of the protection hierarchy highlighted in the following revised figure from the Gartner report.
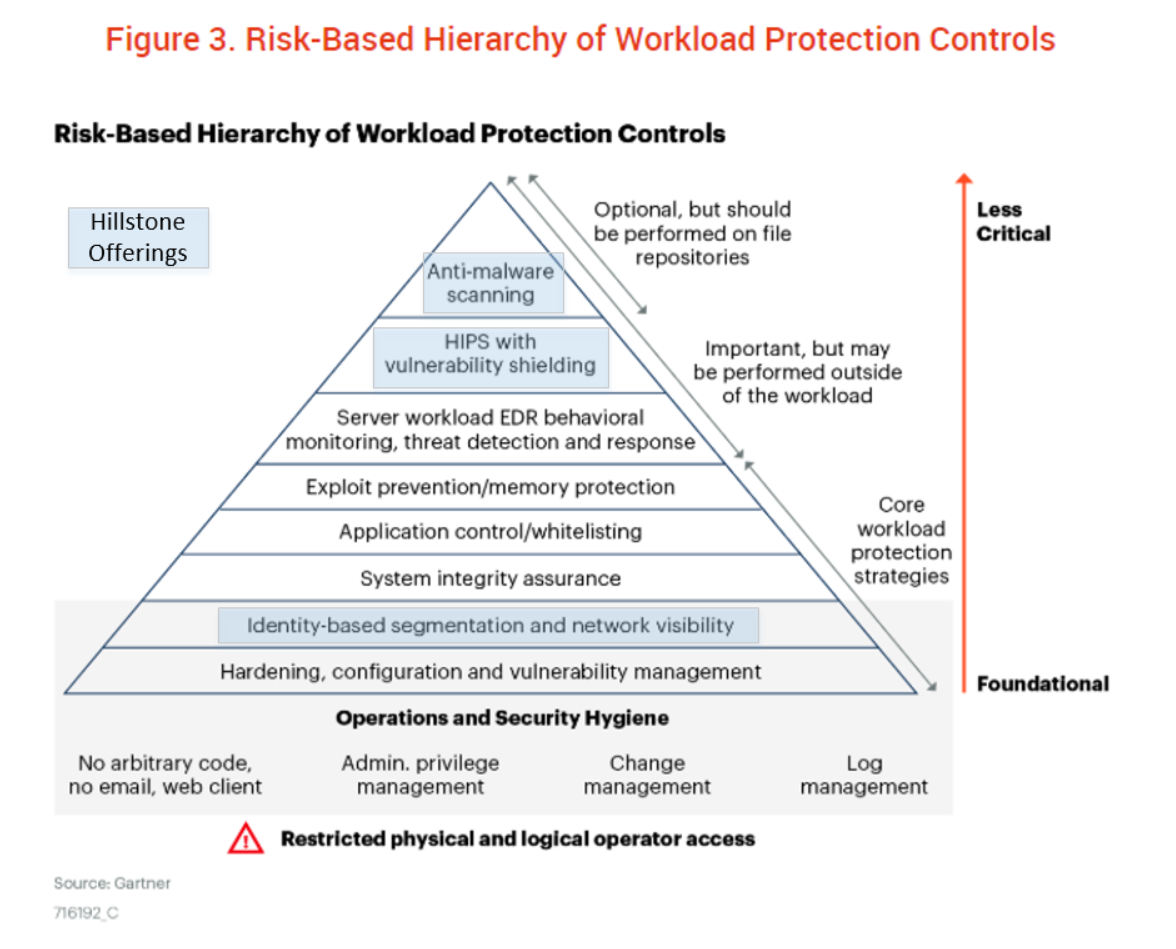
In the report, Gartner also
Hillstone Networks is actively working on security solutions for cloud workloads running on containers, from image and file system vulnerability scanning, to server behavior monitoring, to runtime traffic monitoring and threat detection. In the near future, Hillstone Networks will expand its offerings in the domain of CWPP.
If you are responsible for the cloud protection and hybrid cloud workloads of your organization, CloudHive can provide the micro-segmentation, deep visibility and strong security measures you need to keep your data and network resources protected. Contact your Hillstone authorized reseller or sales representative today to learn more.
*: Gartner, Market Guide for Cloud Workload Protection Platforms, Neil MacDonald, Tom Croll, 14 April 2020
Gartner Disclaimer:
Gartner does not endorse any vendor, product or service depicted in our research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from here.


