Introduction
Apache Commons Text is a library dedicated to string-processing algorithms. A severe 9.8 severity rating has been assigned to the Apache Commons Text remote code execution vulnerability, which allows attackers to execute arbitrary code on a system and compromise the entire host.
Vulnerability
This vulnerability is largely attributable to the improper validation of StringSubstitutor interpolation defaults — a logic flaw that makes the script, DNS and URL lookup keys interpolated by default, as opposed to a strict validation.
The prefix in the Apache Commons Text interpolation format ${prefix:name} is used to locate the instance of org.apache.commons.text.lookup.StringLookup that performs the interpolation. But if the instance contains untrusted configuration values, the attackers can execute malicious code by constructing malicious text. They inject malicious text containing keywords that can trigger a DNS request, a call to a remote URL, or an inline script to execute, so that they can trigger arbitrary code to execute, pulling code from external sources or embedding arbitrary scripts.
Affected Version
1.5 <= Apache Commons Text<=1.9
Remediation
1. Official fix: The vendor has released the patches, and we recommend that users upgrade to Apache Commons Text 1.10.0. Please visit:
https://commons.apache.org/proper/commons-text/download_text.cgi
2. Reference methods on GitHub: We can fix the vulnerability by making default string lookups configurable via system property and removing DNS, URL, and script lookups from defaults. Please visit:
https://github.com/apache/commons-text/commit/b9b40b903e2d1f9935039803c9852439576780ea
Implementing the Fix
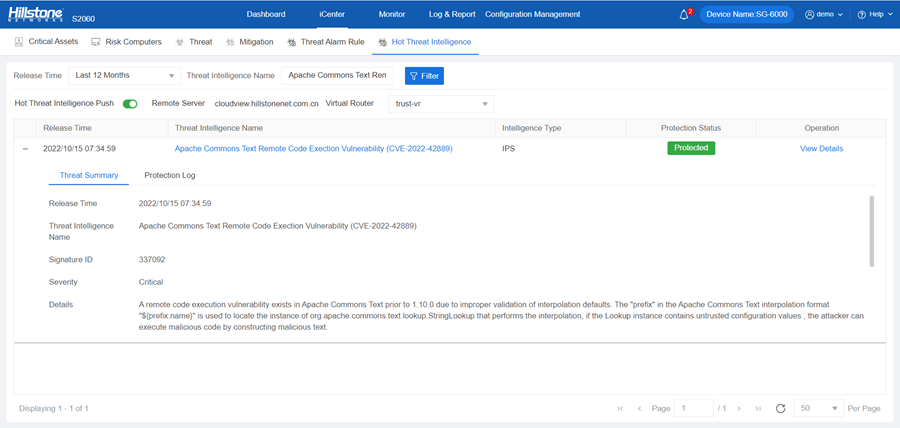
The Hillstone Networks Intrusion Prevention System (IPS) can support the detection and protection of this vulnerability.
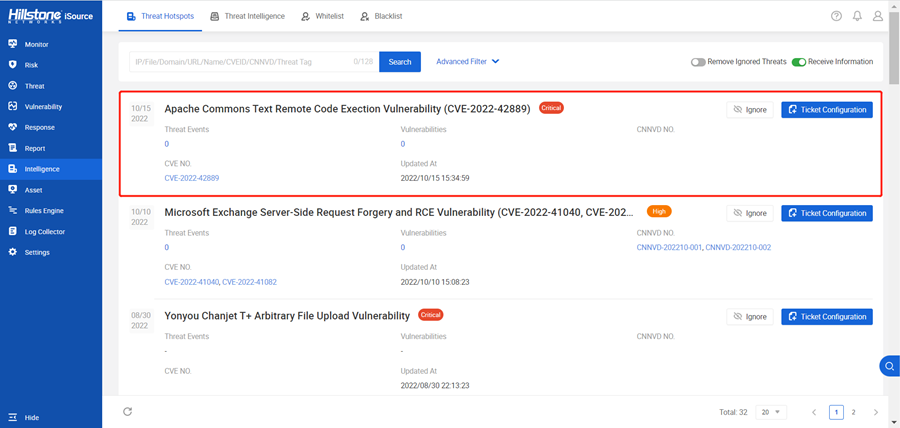
The hotspot intelligence of this vulnerability is available on Hillstone Networks iSource as well.