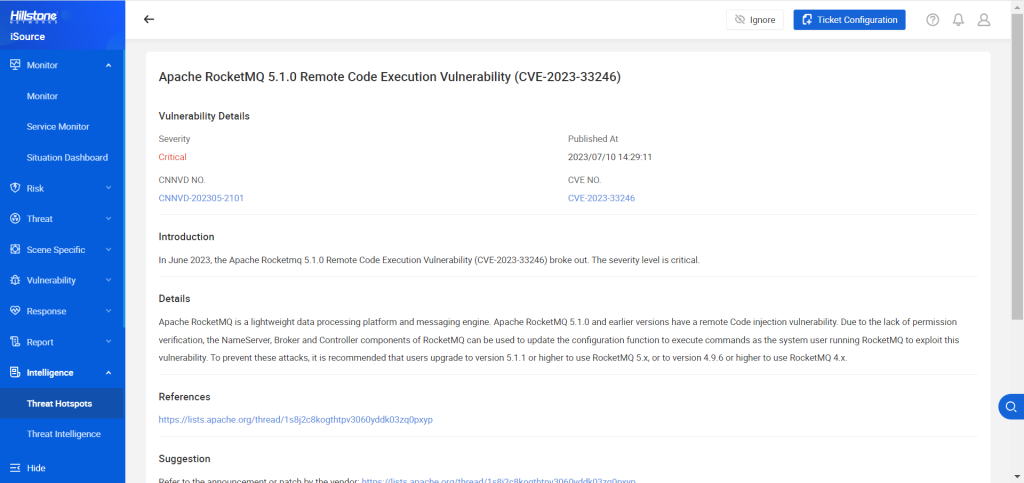
Introduction
Apache RocketMQ, a widely-used, lightweight, low-latency, high-concurrency, highly available, and highly reliable distributed data processing platform and messaging middleware. It has encountered a vulnerability that could potentially expose systems to the risk of remote code execution, namely the Apache RocketMQ 5.1.0 Remote Code Execution Vulnerability, identified by the CVE reference number CVE-2023-33246, which has brought significant concerns to the forefront of cybersecurity.
Vulnerability
The Apache RocketMQ 5.1.0 Remote Code Execution Vulnerability revolves around a sequence of interconnected components within the RocketMQ infrastructure.
Broker is responsible for message storage, delivery, and high availability. Upon initialization, the Broker node registers itself with the NameServer node. The DefaultMQAdminExt class facilitates the retrieval and modification of pertinent configuration information by interacting with NameServer. The FilterServerManager class undertakes the management of Filter Servers. These servers are responsible for handling the registration, updating, and deletion of message filtering rules. Moreover, they evaluate and match message filters. In the heart of this vulnerability lies the FilterServerUtil class’s callShell method. This method employs Runtime.getRuntime().exec(cmdArray) to execute system commands. Crucially, the commands being executed stem from the shellString parameter of this function. This implies that if an attacker can manipulate the shellString parameter of the callShell method, they can potentially achieve remote code execution. This is because the method’s underlying command execution mechanism can be tricked into running arbitrary commands, leading to remote execution of arbitrary code, complete with the associated risks of data breaches, unauthorized system access, and more.
Affected Version
5.0.0 <= Apache RocketMQ < 5.1.1
4.0.0 <= Apache RocketMQ < 4.9.6
Remediation
Official fix: To prevent these attacks, users are recommended to upgrade to version 5.1.1 or above for using RocketMQ 5. X, and version 4.9.6 or above for using RocketMQ 4. x. Please visit:
https://rocketmq.apache.org/download/
Implementing the Fix
Upgrade your IPS signature database to version 3.0.165 and your AV signature database to version 2.1.515 to ensure that Hillstone Networks Intrusion Prevention System (NIPS) and Hillstone Breach Detection System (BDS) are equipped to detect and provide protection against this vulnerability.
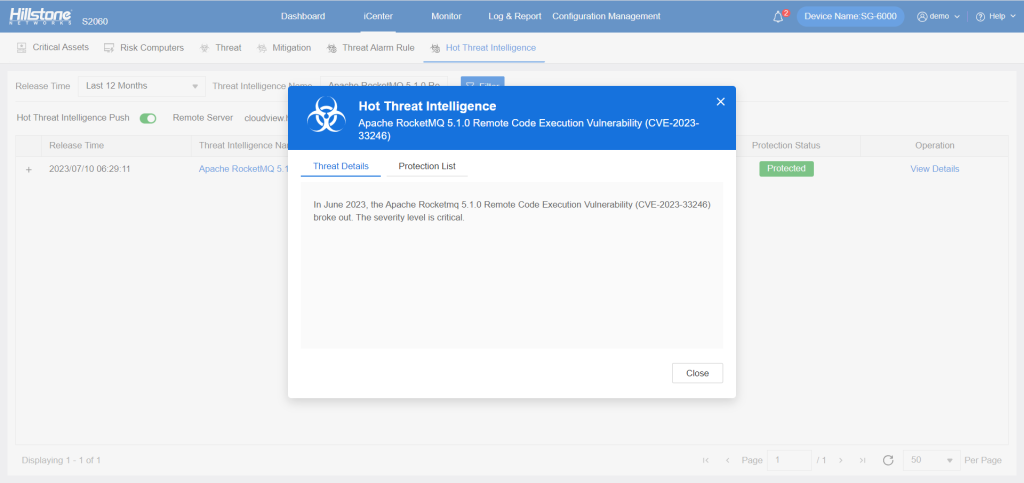
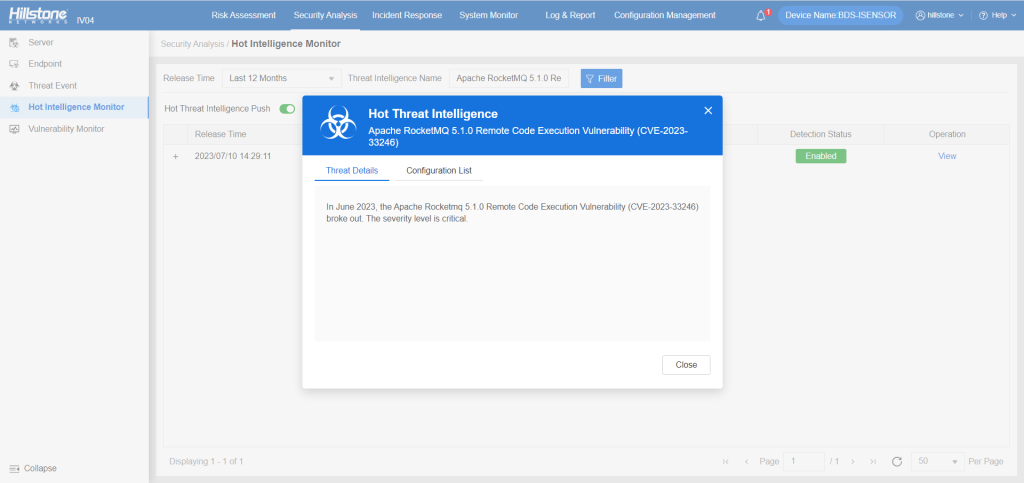
The hotspot intelligence of this vulnerability is available on Hillstone Networks iSource as well.