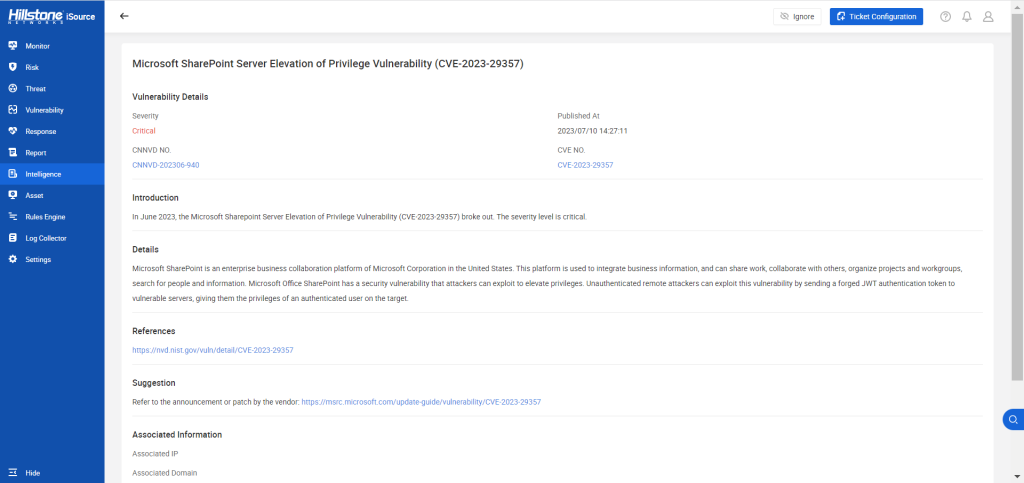
Introduction
Microsoft SharePoint is a widely used enterprise business collaboration platform that facilitates seamless integration of business information, enables work sharing, collaboration, project organization, and effective search capabilities. However, like any sophisticated software, it may also be susceptible to security vulnerabilities. In this blog, we will explore a significant hotspot vulnerability, namely the Microsoft SharePoint Server Elevation of Privilege Vulnerability (CVE-2023-29357).
Vulnerability
This vulnerability revolves around an issue that allows unauthenticated remote attackers to elevate their privileges on the target system.
To comprehend this vulnerability better, we need to understand what is JWT authentication token. JWT stands for JSON Web Token, which is a standard for representing claims securely between two parties. These tokens are digitally signed and can contain various pieces of information about the user or entity that holds them. When a user authenticates on SharePoint, they receive a JWT authentication token, which acts as digital proof of their identity and permissions. The vulnerability allows attackers to create forged JWT tokens that may appear legitimate to SharePoint servers. By crafting such tokens and sending them to vulnerable servers, attackers can bypass authentication checks and gain unauthorized access to the system. Then, attackers trick the system into treating them as legitimate authenticated users. As a result, the attackers’ privileges are elevated, granting them access to sensitive resources, data, or functionalities reserved for authenticated users.
Remediation
Customers who have enabled the AMSI integration feature and use Microsoft Defender across their SharePoint Server farm(s) are protected from this vulnerability. For more information, see:
https://learn.microsoft.com/sharepoint/security-for-sharepoint-server/configure-amsi-integration
Implementing the Fix
Upgrade your IPS signature database to version 3.0.165 and your AV signature database to version 2.1.515 to ensure that Hillstone Networks Intrusion Prevention System (NIPS) and Hillstone Breach Detection System (BDS) are equipped to detect and provide protection against this vulnerability.
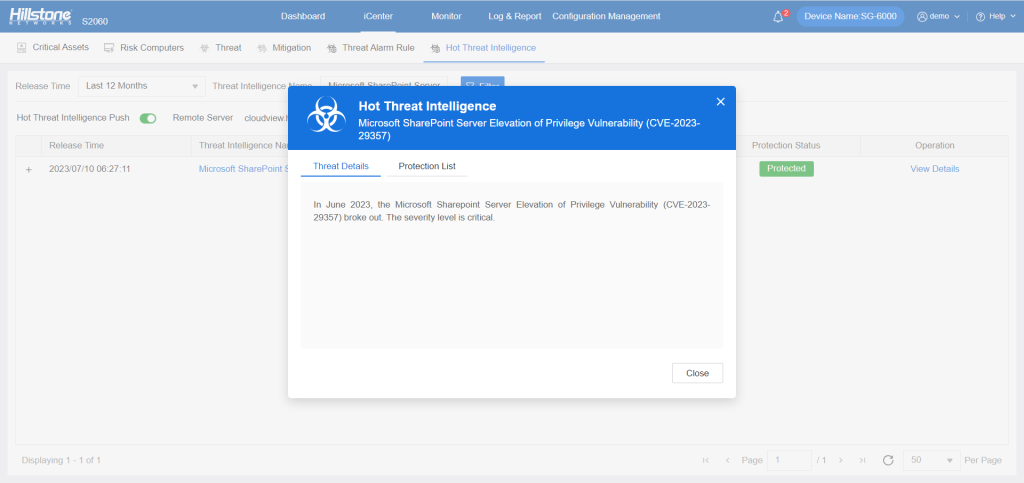
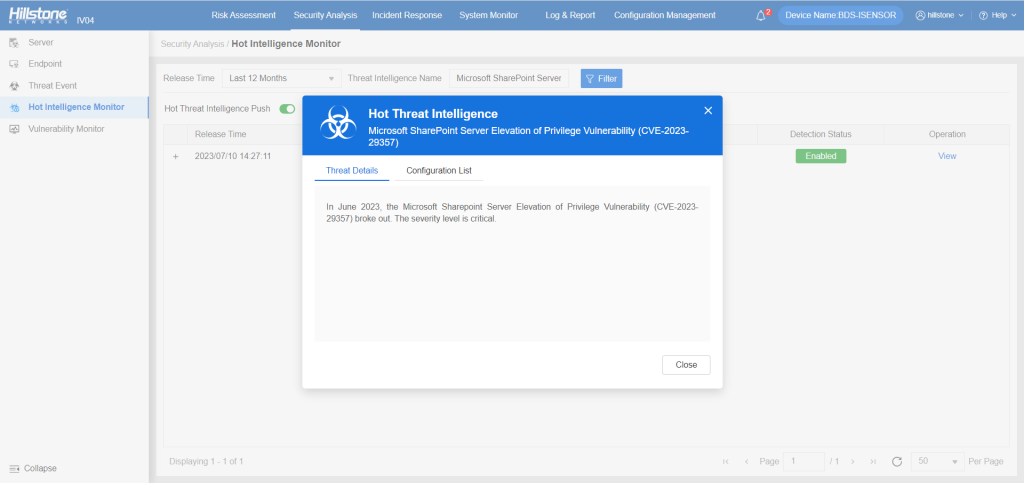
The hotspot intelligence of this vulnerability is available on Hillstone Networks iSource as well.