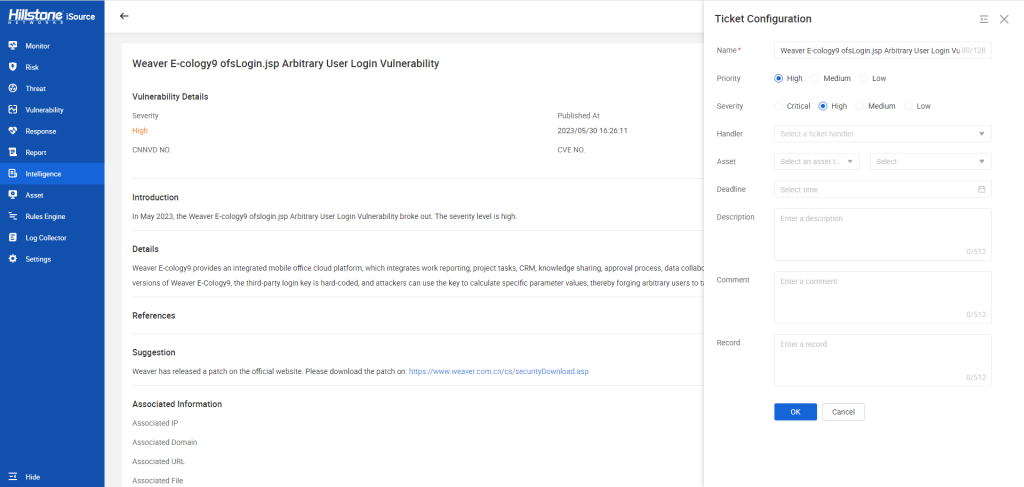
Introduction
Weaver E-cology9 is an integrated mobile office cloud platform that provides a range of applications including work reporting, project tasks, CRM, knowledge sharing, approval processes, and data collaboration. Recently, a high-severity vulnerability was discovered in Weaver E-cology9, which allows attackers to log in as arbitrary users by exploiting a hard-coded third-party login key.
Vulnerability
The ofslogin.jsp vulnerability in the mobile plugin of Weaver E-cology9 allows attackers to exploit a flawed login process. By accessing the ofsLogin.jsp file and providing specific parameters, including syscode, receiver, timestamp, loginTokenFromThird, and gopage, attackers can manipulate the loginTokenFromThird value. If the provided loginTokenFromThird value matches the generated loginTokenFromThird2 value, the login process continues. Subsequently, the syscode parameter is used to query the ofs_sendinfo table, examining the hrmtransrule field. If this field is either empty or set to ‘1’, the loginid field in the HrmResource table is used to search for user information based on the receiver value. Upon successful identification of user information, a session is generated, granting the attacker unauthorized access as the forged user. This exploit enables the attacker to gain complete control over the Weaver E-cology9 platform and its associated privileges.
Affected Version
E-cology9 < V10.57.2
Remediation
Official fix: The vendor has released the patches, and we recommend that users upgrade to E-cology9 V10.57.2 or a later version. Please visit:
https://www.weaver.com.cn/cs/securityDownload_en.html?src=en
Implementing the Fix
The Hillstone Networks Intrusion Prevention System (NIPS) and Hillstone Breach Detection System (BDS) can support the detection and protection of this vulnerability.
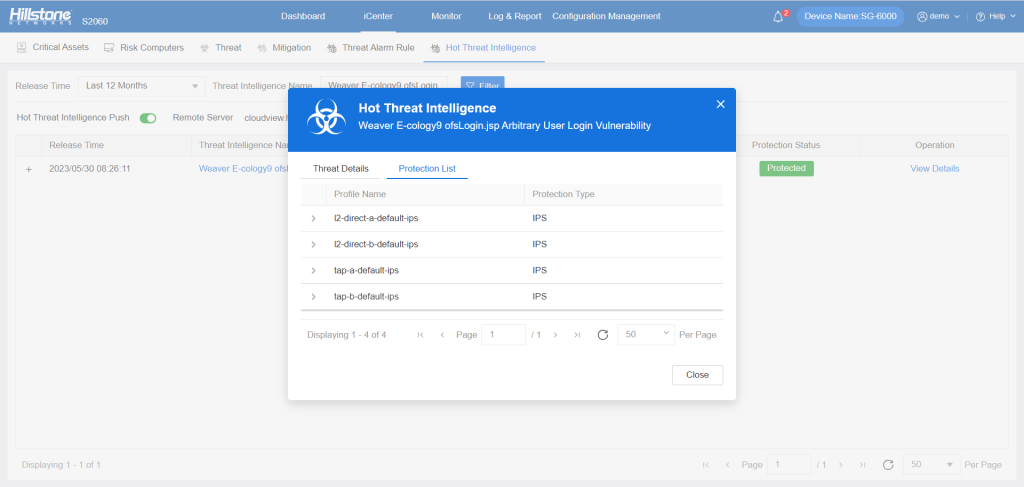
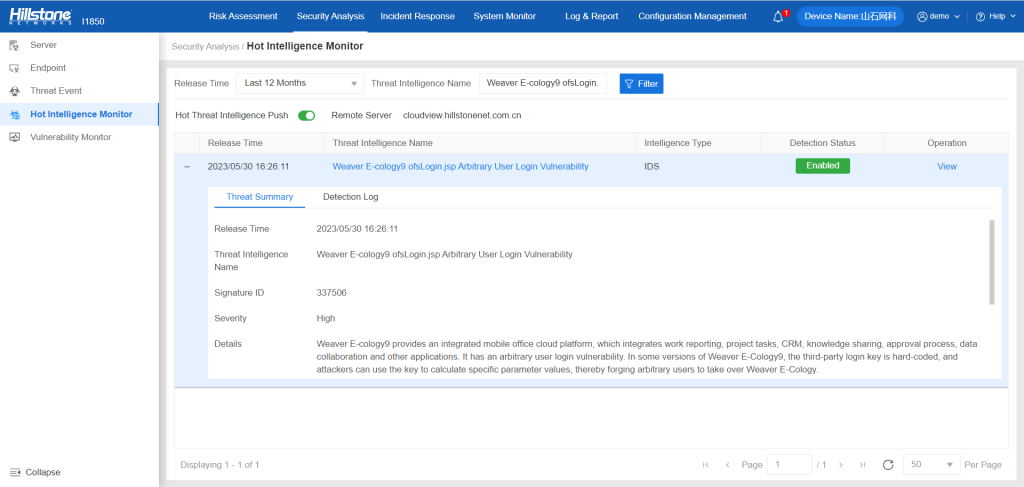
The hotspot intelligence of this vulnerability is available on Hillstone Networks iSource as well.