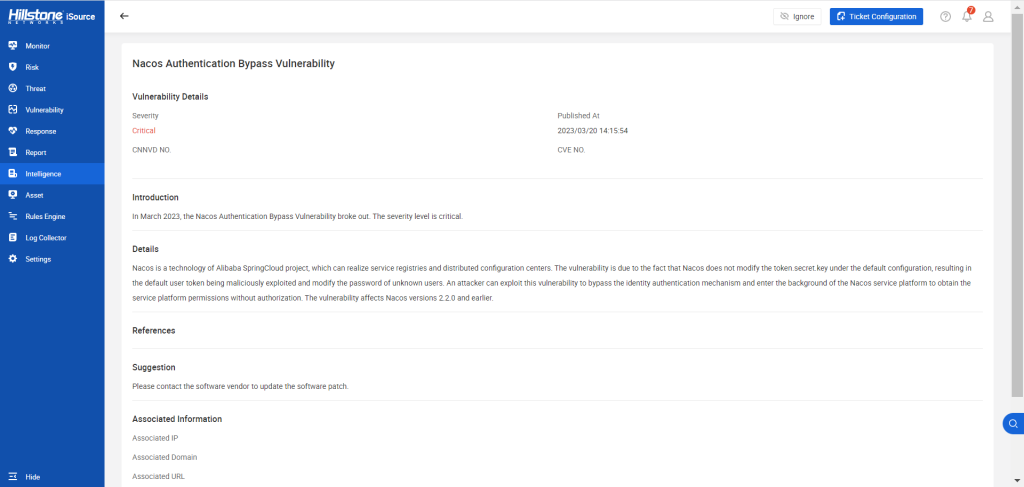
Introduction
Alibaba Nacos is an easy-to-use platform designed for dynamic service discovery, configuration, and management of micro-services. It is an open-source solution commonly used by organizations to manage and configure their micro-services. However, a vulnerability has been discovered in Nacos that may allow hackers to bypass authentication and gain unauthorized access to the system.
Vulnerability
The vulnerability arises from Nacos’ failure to modify the token.secret.key under the default configuration. This flaw enables malicious actors to exploit the default user token and modify the passwords of unknown users. By exploiting this vulnerability, attackers can bypass the identity authentication mechanism and gain unauthorized access to the Nacos service platform, thereby obtaining permissions to the service platform without proper authorization.
If this vulnerability is leveraged, the attackers are granted access to sensitive information or authority to modify system configurations, potentially resulting in a variety of malicious activities, such as data theft, system disruption, or even a complete system takeover.
Affected Version
Nacos version <= 2.2.0
Remediation
Official fix: The vendor has released the patches, and we recommend that users upgrade to Nacos V2.2.1 or a later version. Please visit:
https://github.com/alibaba/nacos/releases/tag/2.2.1
Implementing the Fix
Please upgrade your IPS signature database to version 3.0.150 and your AV signature database to version 2.1.500 to ensure that Hillstone Networks Intrusion Prevention System (IPS) and Hillstone Server Breach Detection System (sBDS) are equipped to detect and provide protection against this vulnerability.
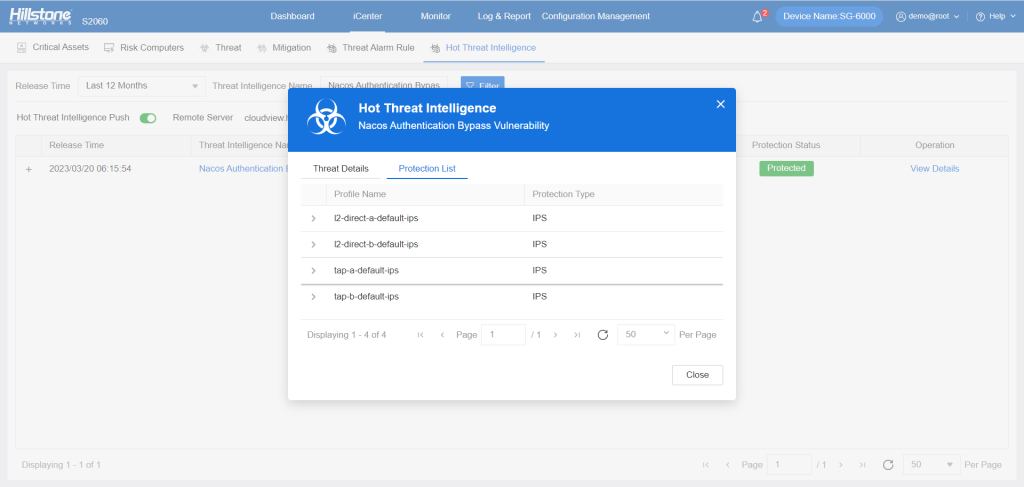
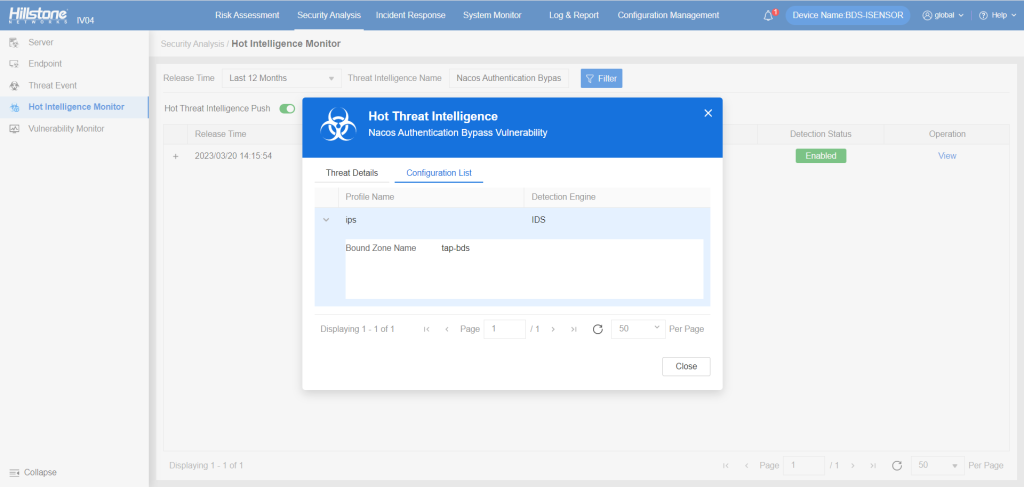
The hotspot intelligence of this vulnerability is available on Hillstone Networks iSource as well.