Introduction
On March 2022, SuiteCRM discovered an email-template remote code execution vulnerability. SuiteCRM is a free open-source customer relationship management application for servers, which can be an alternative for proprietary CRM software such as Hubspot, Salesforce, or others. As a global open-source CRM, it is readily available and frequently used, making this vulnerability even more critical.
Vulnerability
In SuiteCRM versions that are less than 8.0.2 or less than 7.12.3, the email-template modules are able to be compromised via malicious PHP files. Specifically, image tags could be manipulated to be acceptable by the regex established for the function. From here, a new email template can be created using an image tag that can bypass the regex established earlier, but instead, the file name can be changed to a .php file. When the email template is saved and reloaded, the .php file can be executed, enabling remote code execution capabilities for hackers.
Remediation
This vulnerability has been patched via the following adjustment. An “if” statement was added, allowing only valid image file extensions to be used in the email template module. This prevents non-whitelisted extensions, such as .php files, from being created. From this, attackers can no longer illegitimately create a shell for their remote code execution.
Implementing the Fix
Based on the current characteristics of the vulnerability, the following suggestions are highly recommended:
- Reference methods on GitHub: https://github.com/manuelz120/CVE-2021-45897
- The vendor has released upgrade patches to fix vulnerabilities, please visit: https://docs.suitecrm.com/
Hillstone IPS can provide adequate protection against this vulnerability, and the protection can be automatically configured within the device by updating the signature database version to 3.0.98, 2.1.447. False positives are zero to none, making it easy to nullify this vulnerability. The corresponding signature to remediate this vulnerability is signature 336294.
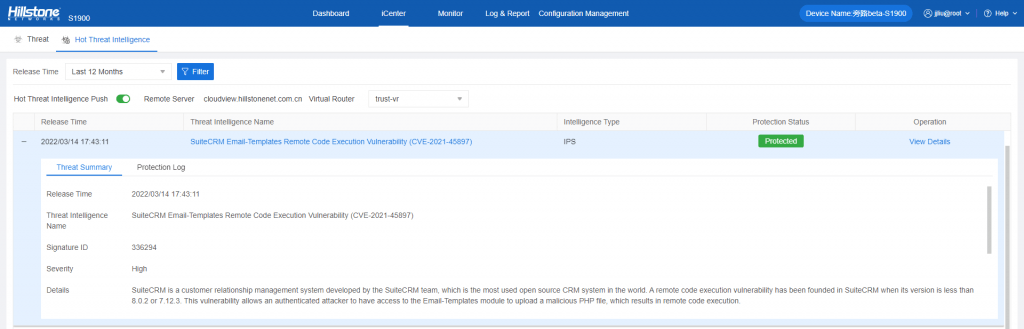
Figure 1. Remote code execution vulnerability resolved by Hillstone IPS
Hillstone BDS can support the detection of the vulnerability.
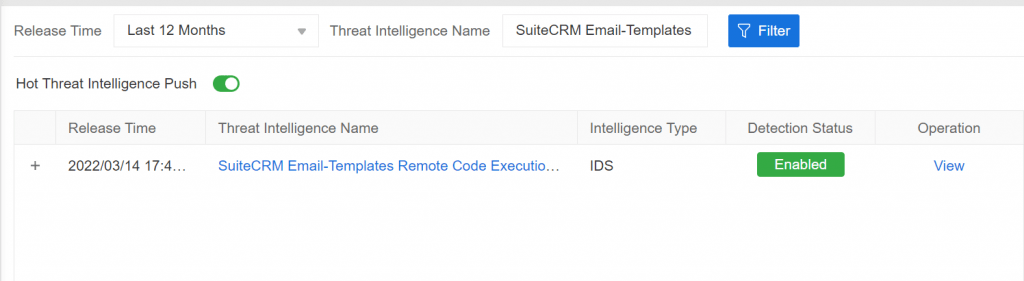
Figure 2. Remote code execution vulnerability detected by Hillstone BDS
The hotspot intelligence of this vulnerability is available on Hillstone iSource as well.
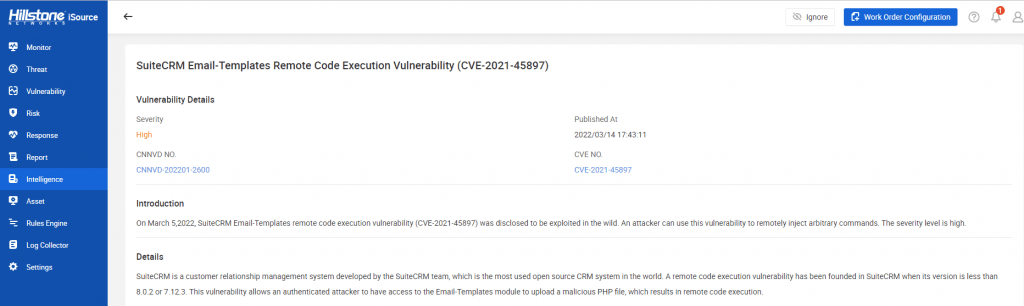
Figure 3. Hotspot intelligence on Hillstone iSource



