In the era of digital transformation, enterprises are adapting their network and security strategies in light of two key trends that accelerated with the arrival of the COVID-19 pandemic. The first is the transition to a wider cloud adoption, and the second is the growth of a highly distributed remote workforce that has reshaped networking and security requirements.
Today, enterprises need to deploy security services freely, anytime and anywhere, with the ability to control and secure the remote workforce as well as internal resources. This means that the traditional network security boundary is gradually disintegrating. However, legacy network security architectures and solutions that are based on the physical boundary are difficult to adapt to the new enterprise networking paradigms. This is when a zero-trust model comes into play.
What is Zero Trust?
According to the definition in the NIST (National Institute of Standards and Technology) special publication, “Zero Trust Architecture*”:
“Zero trust (ZT) is the term for an evolving set of cybersecurity paradigms that move defenses from static, network-based perimeters to focus on users, assets, and resources… Zero trust assumes there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership (enterprise or personally owned)…”
Zero trust is neither a technology nor a product, but a security concept. The essence of zero trust is to build a secure business access environment by eliminating unverified implicit trust in the network. “Never trust, and always verify,” is the core idea of zero trust. The ultimate goal is to grant only the exact amount of access and authority to only trusted users. With zero trust, there is no use of a physical boundary to divide trusted and untrusted users, devices and networks.
Many companies have carried out technical and product development based on the zero-trust model. Zero trust is mostly used to solve the problems of identity management and access control. Zero Trust Network Access (ZTNA) is a part of the zero-trust concept that transforms traditional remote connection methods with finer-grained control, more flexible expansion, and higher reliability.
Why Zero Trust Network Access?
The traditional VPN assumes that any user that passes the corporate perimeter control, or any device that is inside the corporate network, can be trusted. However, ZTNA takes a different approach: no user or device is trusted to access any resources until its identity is fully authenticated, and access to resources is limited to only that which is allowed.
Moreover, a traditional VPN is not easy to scale because it requires manual configuration and massive IP management processes to adapt to constantly changing users and applications. So, with the big rise in roaming users and remote working, Zero Trust Network Access (ZTNA) provides enterprises a better way to control application access and secure their resources, regardless of the users’ physical locations.
ZTNA Can Help Protect Your Data Everywhere
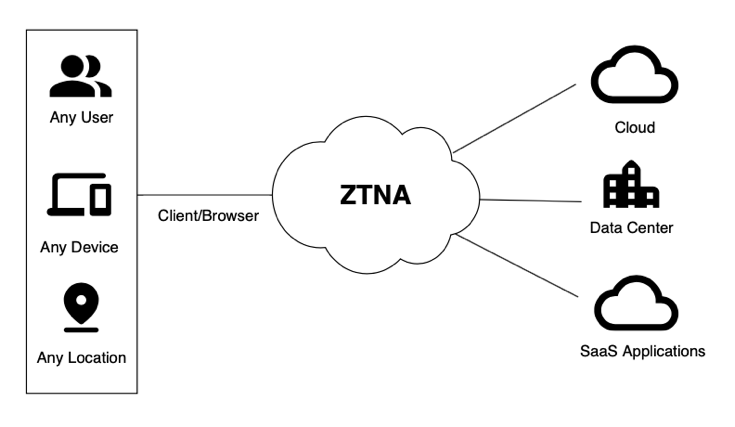
Hillstone believes that ZTNA needs to apply a user-to-application – not network-centric – approach to authenticate security based on the identity and context of the user and device, as well as the resources being accessed. This change in focus extrapolates security from the network perimeter to the cloud and the distributed workforce and allows far easier scaling.
Our conception of ZTNA would provide a holistic view of remote user connections and help configure consistent corporate policies that grant granular access for legitimate users only to the applications and resources allowed within their privilege credentials.
Various user and device attributes, such as the patch level and presence of current antivirus, would be checked and continuously monitored. Once the user and device meet certain requirements, access would be granted to specific applications and resources based upon the user identity.
Further, with a technology like Single Packet Authorization (SPA), no services in the data center or SaaS applications would be exposed to the public network, and would be invisible to unauthorized users.
The trends that have been accelerated by COVID-19 – wider cloud adoption as well as growth of the distributed workforce – have mandated a reshaping of networking and security requirements. ZTNA, if executed properly, has great potential to extend cybersecurity anywhere and anytime to control and secure the remote and local workforce while protecting internal and cloud resources.
*Rose, S. , Borchert, O. , Mitchell, S. and Connelly, S. (2020), Zero Trust Architecture, Special Publication (NIST SP), National Institute of Standards and Technology, Gaithersburg, MD, [online], https://doi.org/10.6028/NIST.SP.800-207, https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=930420 (Accessed September 28, 2021)



