WikiLeaks founder Julian Assange was arrested at the Ecuadorian Embassy in London after Ecuador withdrew their asylum status after seven years. In response to the arrest, activist communities launched several attacks against the Ecuadorean government. Yesterday, Ecuador confirmed that over 40 million cyberattacks have hit public institutions in response to the arrest of Julian Assange.
The following is a snapshot of cyber threats, a real-time attack map from Kaspersky Security Network illustrating the cyber-attacks relating to the incident.
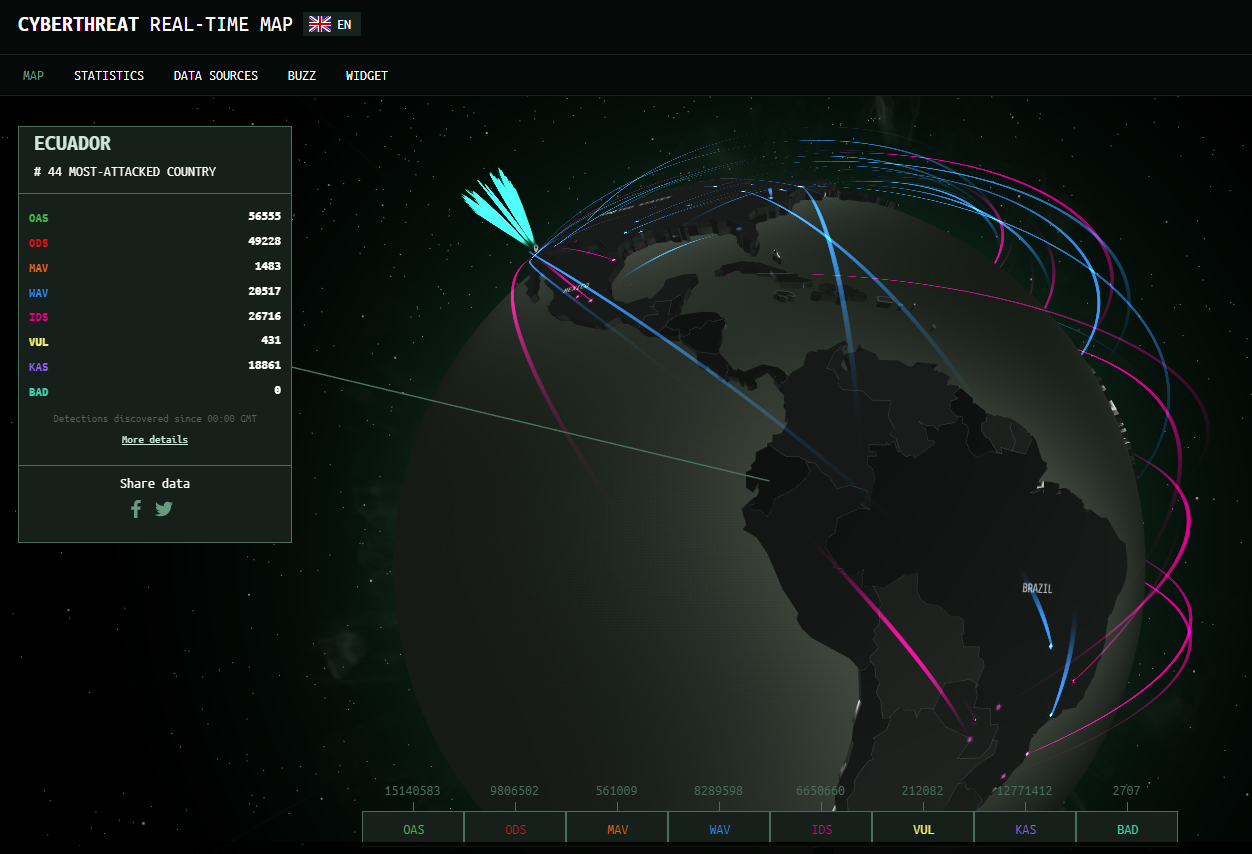
This real-time attack map displays the statistical data and the top threat categories on infected machines detected by anti-virus, anti-spam detections mechanisms and other diagnostic tools used in Kaspersky’s research lab.
Setting the associated political factors aside, in today’s connected world, it’s clear that cyberattacks can be launched from disparate sources and locations on the planet, spreading from individual hackers, organized groups or organizations all the way up to the level of state sponsored attacks. The purpose of these attacks also varies, ranging from leisure know-how brags, to Advanced Targeted and Persistent (APT) attacks, and from monetary or financial gains to other politically motivated or economic reasons.
Moreover, the tools that are used in these attacks are also becoming more sophisticated; they can easily get by the conventional security measures usually deployed at network perimeters.
As stated, there are many different kinds of cyber-attacks. Here, I’ll provide some general information using what is called the attack chain model, the Kill Chain, which is widely used in the security industry to illustrate each stage of an attack in progress.
To penetrate the security defense at the network border, hackers typically leverage social medias or phishing emails with malicious attachments inside files. Once the hacker lands inside the network, the behaviors of malicious software usually include hibernating for certain periods of time, sometimes for a long period of time, to avoid immediate correlations in security policies and detection. Study shows that the average hiding time for a typical APT can last to about 200 days. It then conducts internal reconnaissance activities to locate critical servers or applications from which to steal confidential data. It can then try to gain access using privileged escalations, brute force methods or other mechanisms. After gaining access to critical assets, they perform data exfiltration to send the stolen data to external servers.
On another note, ransomware attacks have become more popular today due to the fact that hackers can quickly gain financial benefits from the victim organizations by encrypting their data and files needed for normal business activities, and demanding ransom payments in exchange for decryption keys. Most businesses would just pay the ransom to get the locked data restored and continue with normal business.
As the results, traditional cyber security defenses at the network border prove to be ineffective since a typical APT usually involves many stages over a prolonged period of time. Security defenses against modern cyber criminals with sophisticated weapons and tools requires detecting and throttling these attacks from all angles and at different stages during the attacking progress.
Hillstone Networks is a global leading security vendor and offers comprehensive security detection and protection products and solutions at multiple layers that protect enterprises and organizations at different network and user endpoints, network gateways, as well as in the cloud.
For security defense at network perimeter, Hillstone’s NGFW and NIPS solutions provide conventional firewalls and signature based threat detections against existing and known attacks. All NGFW functions are integrated in this product category including anti-virus, anti-spam, app-ID, URL filtering, DNS security and IP reputations. NGFW also integrates with a cloud sandbox that can be used to detect unknown attacks or near 0-day attacks.
Hillstone Networks also has internal network security solutions- Server Breach Detection System (sBDS) using behavioral analysis (UEBA), network traffic analysis (NTA), deception techniques and big data analysis using machine learnings and other statistical analysis mechanisms. The sBDS platform is usually deployed in tapping mode close to the critical servers it protects, meaning it will not interfere with normal business traffic, and is placed near the servers it tries to protect inside a corporate network. It conducts traffic analysis and threat detection using the mirrored traffic. The detailed threat detection and analysis results are presented in the iCenter dashboard, which delivers deep visibility and provides knowledge base for the detected threats and attacks. The sBDS platform can also integrate with Hillstone’s NGFWs to provide threat mitigations on demand.
Sophisticated cyber-attacks require comprehensive and layered security protection. Hillstone Networks has a wide range of effective weapons in its arsenals to enable companies and organizations in fighting against cyber criminals and cyber-attacks.
About Author
David Yu is a distinguished engineer at Hillstone Networks. He is the leading software architect of Hillstone’s distributed firewall product, the awarding winning intelligent NGFW (iNGFW) and intranet server protection (sBDS) products. He also lead efforts in product developments and technology promotions of Hillstone’s advanced threat detection and protection based on behavioral analysis, network traffic analysis, big data analysis using machine learning and cloud security infrastructures. He has previously worked for IBM, 3Com, Juniper Networks and has over 20 years experiences in networking and security industries.


