Before discussing SSL (Secure Sockets Layer) encryption, recall when you’ve visited websites, and wondered why a domain name starting with HTTP is denoted as unsafe, whereas a domain name starting with HTTPS is denoted as safe.
HTTP and HTTPS, which are two different request methods, lead to different results. Why is HTTPS safe? There has to be something more than just the extra letter “s”.
What is HTTPS?
HTTPS is commonly referred to as HTTP in an SSL shell. HTTPS is a transport protocol for secure communication over computer networks via HTTP, which uses SSL/TLS to establish all channels and encrypt packets.
The primary purpose of HTTPS is to provide authentication to the web server while protecting the privacy and integrity of the data being exchanged.
PS: TLS is a transport layer encryption protocol, the successor to SSL protocol, released in 1995 by Netscape Corporation. However, due to the pseudonym already being established, users still use the terms SSL and TLS interchangeably.
For a better understanding of HTTPS, cryptography, the study of mathematical techniques related to aspects of information security, should be introduced. One major concept within the field of cryptography that is pertinent to our discussion of HTTPS is “encryption”. Encryption techniques are categorized into symmetric and asymmetric encryption techniques.
Symmetric encryption is the fastest and simplest way of encryption, where the same secret key is used for encryption and decryption. The method is referred to at times as a “shared secret”. There are many algorithms for symmetric encryption (e.g., AES, DES, etc.), and it is widely used in the core of many encryption protocols because of its high efficiency. However, one of the significant drawbacks of symmetric encryption is the management and distribution of the key. In other words, it is problematic to send the key to the person who needs to decrypt your message. There is a high risk that hackers will intercept the key during that process.
Asymmetric encryption provides a very secure method for encrypting and decrypting data. It uses a pair of keys – a public key and a private key. Whereas the private key is known only to one party, the public key can be shared with anyone who requests it. Both keys are required in order to access an encrypted set of information. Asymmetric encryption uses one of a pair of keys for encryption (public key), and another set of keys (private key) for decryption. Its commonly used algorithms include RSA and ECDSA. Although asymmetric encryption is secure, it is very slow in comparison to symmetric encryption.
Hybrid encryption combines the advantages and disadvantages of asymmetric encryption and symmetric encryption technology for practical applications. It means that the symmetric encryption key is encrypted using the public key of asymmetric encryption, and then sent out. The receiver uses the private key to decrypt and receive the symmetric encryption key. Then, both parties can use symmetric encryption to communicate. In this scenario, even if communication is intercepted by hackers, the plaintext data cannot be obtained because hackers don’t possess the private key necessary to receive the symmetric key used to encrypt the plaintext. By integrating elements of asymmetric encryption with symmetric encryption, the speed of encryption/decryption is expedited while retaining the ability to ensure security of the transmitted content.
The following image illustrates the SSL interaction process.
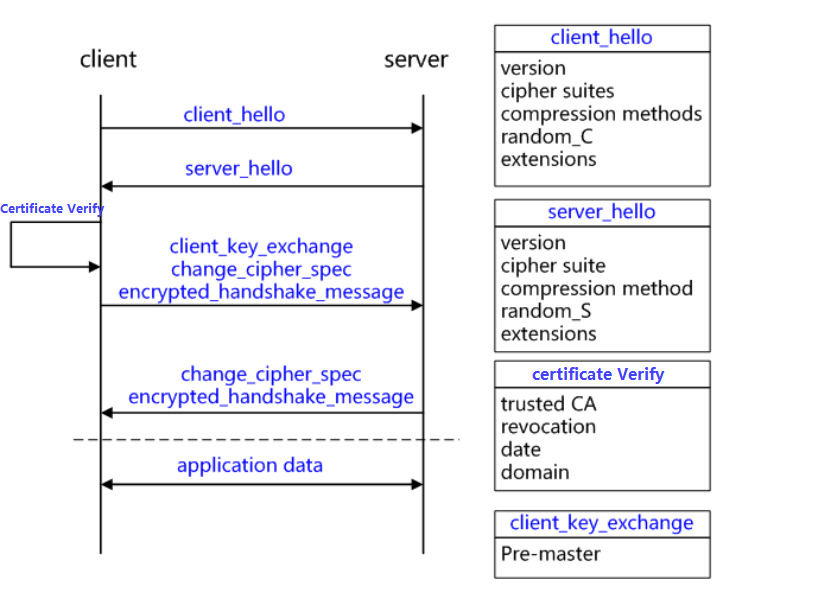
Why use HTTPS?
HTTPS with hybrid encryption has the following characteristics:
- Content encryption: Man-in-the-middle cannot view the plaintext directly.
- Authentication: Authenticate the client to access its server through a certificate.
- Data integrity: Prevent Man-in-the-middle from impersonating or tampering with the content during transmission.
Chrome 56, released in January 2017, began marking HTTP pages that collect passwords or credit card data as unsafe. If users use Chrome 62, introduced in October 2017, HTTP pages with input data and all HTTP pages viewed in a streak-free mode will be marked as unsafe. In addition, Apple transitioned all iOS apps to use HTTPS encryption by January 1, 2017.
Websites Upgrade to HTTPS
There are two main options for upgrading a website from HTTP to HTTPS:
- Upgrade through server deployment
Change all the links in the website pages in the server, such as js, css, images, etc., from HTTP to HTTPS.
Although the method works, there are several problems:
- Modifying all the links on the website to HTTPS is a lot of work, and some users are unable to maintain the website code, so they need to find the original website developer to modify it.
- After HTTPS is enabled, because a server does not natively possess hardware acceleration cards for encryption and decryption, encryption and decryption can be very costly to server performance. The server may be overloaded, resulting in poor business, or even worse, result in a break in business continuity. The financial and labor costs of replacing a higher performance server to redeploy the service could potentially skyrocket.
- Upgrade via SSL OffLoad device
By using the SSL OffLoad device, the encryption and decryption work is assigned to a dedicated device, and the original server hence no longer needs to be modified. The SSL OffLoad device has high-powered hardware acceleration cards that can significantly improve the performance of SSL encryption and decryption.
Solution value and main advantages:
- Hillstone Application Delivery Controller (ADC), a professional SSL OffLoad Appliance, is able to support both RSA and ECC commercial certificates, perfectly matching customer certificate types.
- With professional hardware acceleration cards, Hillstone can ensure high performance of the device delivered.
- Support SSL Session id and SSL Ticket session reuse to reduce SSL handshake interaction process and improve SSL negotiation speed.
- Support TCP session reuse function to reduce the number of new and concurrent servers and reduce server pressure.
- If the customer has a limited number of IP addresses, the Hillstone device can support multiple certificates simultaneously with the same IP+PORT to help customers save IP resources.
- Detailed SSL Verify function to verify the correctness of client certificate and improve the security of a customer’s business.
- Support OCSP (Online Certificate Status Protocol) to verify the validity of the client certificate in real time.
- Support OCSP Stapling, the browser does not need to verify the certificate status itself. Instead, the website queries the OCSP server and caches the response, and then returns the response during TLS connection with the browser, which improve the SSL interaction performance.
- It has a simple and convenient certificate chain import mode, and supports PKCS#7, PKCS#12, PEM three formats.
Solutions for Secure Email deployed by SSL cryptography
As the largest contributor of traffic and the most commonly used application on the Internet, E-mail occupies an important position. However, like HTTP, E-mail transmission is plain text transmission. Every email is a “postcard.” People would never include confidential information on a postcard, but digitally, when people use email, they are broadcasting sensitive information about work and about their personal lives.
Normally, data sent between mail servers and mail clients is sent in plain text—leaving you vulnerable to eavesdroppers. Ensuring an email will not be tampered with and instead be transmitted securely is an urgent problem to be solved.
Email service upgrade on SSL cryptography is the same as that of the HTTP service, including upgrading SSL capabilities on the server and using the SSL OffLoad device to redistribute SSL encryption services externally.
Hillstone’s advantages in Email SSL cryptography:
- Hillstone’s application delivery controller supports multiple mail protocols, including IMAP, POP3, SMTP, and IMAPS, POP3S, and SMTPS encrypted by SSL, meeting customers’ requirements in various scenarios.
- Supports multiple transmission modes, including plaintext, ciphertext, and STARTTLS.
STARTTLS: an extension of plaintext communication protocol, which can make the plaintext communication connection directly become an encrypted version (encrypted by SSL or TLS) without using another special port for encrypting. This is a form of opportunistic encryption (OE).
- It can be configured to provide support to peripheral devices and disable insecure SMTP commands, such as the VRFY, EXPN, and TURN commands.
- VRFY: Used to verify the existence of a given user’s mailbox and receive detailed information about that user;
- EXPN: Used to verify the existence of a given list of mailboxes;
- TURN: Can exchange the roles of sender and receiver. This command is usually used when the cost of establishing a connection is high, so ordinary TCP connections do not use this command. Since this command would create security issues, it should only be used if the server can be authorized as a client.
Hillstone’s solution has a lot of successful practices in many areas, such as higher education, telecommunication operators, and so on. With its simple deployment mode, affordable price and excellent capability, our solution has been well received and affirmed by customers. To learn more about Hillstone’s perimeter security products, visit our website, or contact your local Hillstone representative or authorized reseller now!



