1. Introduction
The cyber kill chain[1], put forth by Lockheed Martin, is essentially a cybersecurity model that traces the stages of a cyber-attack. It has been remarkably successful in helping security teams defend against cyber-attacks. But, the cyber kill chain has known limitations, such as its insufficient capability of tracing host attack behaviors. To defend against modern multi-stage and multi-layer cyber-attacks, security teams need to trace network attack behaviors and host attack behaviors as well. As such, the open-source security community began developing the MITRE ATT&CK framework. The MITRE ATT&CK framework retains key features of the cyber kill chain, and additionally provides substantial support to trace host attack behaviors. The MITRE ATT&CK framework is effectively a revolutionized cyber kill chain that is more capable of embracing cyber-resiliency to withstand more modernized threats.
In this blog, we first discuss how the cyber kill chain helps us visualize threat vectors, understand the cyber-attacks, and develop the necessary detection and mitigation strategy. Later, we will discuss how these methodologies are adjusted to better fit the MITRE ATT&CK framework.
2. The Cyber Kill Chain
The cyber kill chain was put forth by Lockheed Martin to trace a targeted cyber-attack. The cyber kill chain has seven attack stages as shown below:
Reconnaissance:
In this stage, an attacker probes an enterprise network to discover vulnerable targets. Targets can be open ports on the network, vulnerable computer software, or emails of enterprise users.
Weaponization:
In this stage, an attacker constrcuts the payload, such as a phishing email or other exploits.
Delivery:
In this stage, an attacker sends the payload built during the weaponization stage to targets identified during the reconnaissance stage.
Exploit:
In this stage, vulnerable computers, or unsuspicious users, open and unknowingly execute the attack payloads.
Installation:
When exploits are successfully executed, more malicious software is installed on the targets to tenaciously continue the attacks.
Command and Control:
In this stage, the malicious software creates covert channels to Command and Control servers. The attacker can control compromised computers via these covert channels.
Actions:
In this stage, the malicious software carries out further actions according to an attacker’s instruction via the C&C servers established in the previous step.
2.1 Analyze and Mitigate Attacks
The success of the cyber kill chain lies in its simplicity. The cyber kill chain has only 7 stages, which capture abstractions of all the attack behaviors well. It is very time consuming to analyze and defend against individual attack behaviors since they are very different from each other. Instead, with the cyber kill chain, security researchers can categorize attack behaviors by the various cyber kill chain stages. From there, researchers can analyze and defend against the categories of attack behaviors as described by the cyber kill chain stages.
A typical process to analyze and mitigate attack behaviors is as following:
- Map attack behaviors into kill chain stages and understand the behaviors based on descriptions of the kill chain stages
- Initiate detection and mitigation strategy for the attack behaviors as suggested by the corresponding kill chain stages
- Prioritize execution via detection and mitigation tasks
There are plenty of guidelines to describe the kill chain stages[1,2,3]. A few guidelines are also available to suggest detections and mitigations[2].
The 3rd step is crucial. Because resources are always limited, a security team has to prioritize certain responses to cyber-attacks. Two principles to prioritize tasks are listed below:
- Prevention is better than detection
An attack that has been prevented is an attack that has completely been nullified. No damage is done to the systems, and no cleanup is necessary. As such, prevention is preferred over detection. Note that prevention is only possible under certain scenarios at early stages, such as Reconnaissance, Delivery and Exploit. At Installation, and Command and Control stages, malware cause permanent modifications to systems. Therefore, by definition, “prevention” is no longer in the cards..
On the contrary, if an attack is detected, but not prevented, the security team will need to initiate post-breach mitigation strategy. Further investigation and clean-up of the any infected systems may be needed. Additionally, a security team can study the attack later to improve its security posture.
- Fix earlier, cost less
If an attack is detected during the early stages of the kill chain, the attack will cause less damage. Regardless, a security team should still investigate and clean up the attack as soon as possible, since the attack may cause more damage over the time if not mitigated in a timely manner.
A common question posed is: “How do we map so many attack behaviors to the correct kill chain stages”? Indeed, mapping attack behaviors to the proper cyber kill chain stages is a prerequisite to performing analysis and mitigation. This is a non-trivial task. Fortunately, many security products supports the cyber kill chain. Each detected attack behavior carries a kill chain stage label. Therefore, a security team doesn’t need to map attack behavior to each kill chain stage as this is already done by the security products they use.
2.2 Limitation:
Present-day attacks utilize encryption over the network, thereby rendering attack behavior detection via the network very difficult. To help with this process, enterprises deploy host security products alongside the network security products. The host security products include traditional AV, Endpoint Detection and Response (EDR), and Endpoint Protection Platform (EPP). Many companies additionally deploy eXtended Detection and Response (XDR), which collects various endpoint/network behaviors and application/services logs to be examined comprehensively.
A shortcoming of the cyber kill chain is that it focuses on network attack behaviors, but not on host attack behaviors. To overcome this limitation, the open-source security community is developing a new cyber security model, the MITRE ATT&CK framework[4], to keep up with modernized security needs.
3. MITRE ATT&CK framework
The MITRE ATT&CK framework has gained a significant amount of recognition in recent years. The MITRE ATT&CK framework offers three major areas of improvements over the cyber kill chain:
- Substantial coverage on host attack behaviors
- Granular description of attack behaviors
- Detection and Mitigation strategies for attack behaviors
1. MITRE ATT&CK tactic
First, the MITRE ATT&CK framework retains the cyber kill chain stages. The stages of the cyber kill chain are mapped to the 14 tactics of the MITRE ATT&CK framework on a 1:1 basis. The 8 new MITRE ATT&CK tactics describe host attack behaviors and are mapped to the ACTION stage of the cyber kill chain. In essence, the MITRE ATT&CK framework is an expansion of the action stage of the cyber kill chain. Also note that the MITRE ATT&CK framework uses unique tags to label tactics as shown in the 3rd column. The MITRE ATT&CK framework also uses unique tags for techniques, detection and mitigations, which will be discussed later.
2. MITRE ATT&CK Technique
The MITRE ATT&CK framework introduces techniques, which described attack behaviors in great detail. There are a total of 245 MITRE ATT&CK techniques, which are nested under 14 tactics. For example, Credential Access tactic (TA0006) possesses 15 nested techniques. Brute force attack RDP service (Brutal Force T1110) is a behavior of credential access attack. Dumping/etc/shadow in Linux (OS Credential Dumping T1003) is another behavior of credential access attack.
3. Analyze and Mitigate Attacks
The MITRE ATT&CK framework not only describes attack behaviors, but suggests detections and mitigations[5] as well. Compared to the cyber kill chain, detection and mitigation recommendations are much better organized. They are versioned and maintained with unique tags for identification. They can be easily cross-referenced with the MITRE ATT&CK tactics and techniques. The following figure is taken from[6]. For the technique OS Credential Dumping: /etc/passwd and /etc/shadow (T1003.008), the framework suggests the following mitigation strategies:
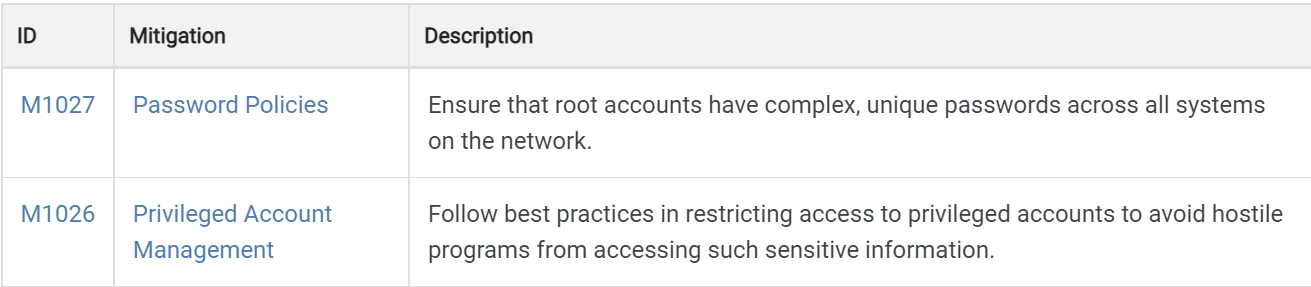
Figure 1. Mitigations for MITRE ATT&CK technique T1003.008
The MITRE ATT&CK strategy of analyzing and mitigating attack behaviors is similar to that of the cyber kill chain.
- Map attack behaviors into the MITRE ATT&CK tactics and techniques and understand the behaviors based on descriptions
- Adopt detection and mitigation strategy on the attack behaviors suggested by the MITRE ATT&CK framework
- Prioritize execution via detection and mitigation tasks
Security products are now also supporting the MITRE ATT&CK framework. The detected attack behaviors are labeled with MITRE ATT&CK framework technique tags.
4 Conclusion:
The MITRE ATT&CK framework extends the capability of the cyber kill chain. It provides substantial coverage on host attack behavior and provides more comprehensive descriptions on attack behaviors and suggestions for detection and mitigation. A security team can leverage the MITRE ATT&CK framework to fight against the latest cyber-attacks.
5. Reference
- Maria Korolov and Lysa Myers, What is the cyber kill chain? Why it’s not always the right approach to cyber attacks, https://www.csoonline.com/article/2134037/strategic-planning-erm-the-practicality-of-the-cyber-kill-chain-approach-to-security.html
- Pratik Dholakiya, What Is the Cyber Kill Chain and How It Can Protect Against Attacks, https://www.computer.org/publications/tech-news/trends/what-is-the-cyber-kill-chain-and-how-it-can-protect-against-attacks
- Cyber Kill Chain: Understanding and Mitigating Advanced Persistent Threats, https://www.exabeam.com/information-security/cyber-kill-chain/,
- Enterprise Matrix, https://attack.mitre.org/matrices/enterprise/
- Enterprise Mitigations, https://attack.mitre.org/mitigations/enterprise/
- OS Credential Dumping: /etc/passwd and /etc/shadow, https://attack.mitre.org/techniques/T1003/008/