To assure the security of sensitive data when being transmitted over the Internet, more and more websites adopt SSL encryption to protect their information. For the traditional security devices, they cannot scan the encrypted data, therefore cannot identify, and filter the data. To address this problem, the system provides the SSL proxy function to decrypt SSL encrypted traffic.
SSL proxy, also known as SSL decryption or SSL inspection, is a feature commonly found in modern network security appliances. It allows the Next Generation Firewall to inspect and filter encrypted SSL/TLS traffic.
When SSL proxy is enabled on the firewall, it intercepts SSL/TLS-encrypted traffic passing through the network. This encrypted traffic can include secure web traffic (HTTPS), email (SMTPS/POP3S/IMAPS), and other SSL/TLS-protected protocols.
Here’s how SSL proxy functions in a Hillstone Networks Firewall appliance:
Decryption: The SSL proxy decrypts the incoming SSL/TLS traffic using a root SSL certificate that is installed on the firewall. This certificate is used to generate a new SSL/TLS certificate for the destination server, and the traffic is then re-encrypted using this new certificate. This process is transparent to both the client and the server, and they remain unaware of the interception.
Content Inspection: With the traffic decrypted, the firewall can inspect the content of the data packets, including application layer data. This enables the firewall to apply various security policies, such as URL filtering, antivirus scanning and intrusion prevention, to the decrypted traffic. This is crucial for detecting and preventing threats and malicious content that may be hidden within encrypted traffic.
Re-Encryption: After the inspection and any necessary security policies are applied, the firewall re-encrypts the traffic using the original SSL/TLS certificate intended for the destination server.
Forwarding: The firewall then forwards the re-encrypted traffic to its intended destination, such as a web server or browser client. The destination receives the traffic as if it had been encrypted by the original server/client.
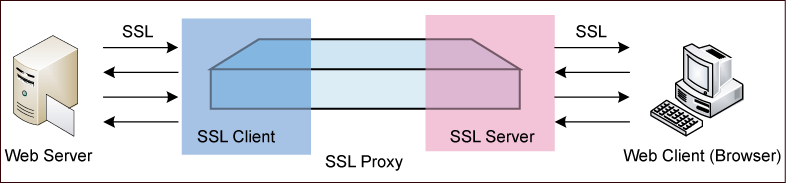
As described above, the SSL proxy function replaces the certificates of encrypted websites with the SSL proxy certificate to get the encrypted information. During the process, the security appliance acts as a SSL client and SSL server to establish connections to the Web server and Web browser respectively. The SSL proxy certificate is generated by using the device’s local certificate and re-signing the website certificate.
By performing SSL/TLS inspection, the Hillstone Networks Next Generation Firewall can provide enhanced security by detecting and preventing threats in encrypted traffic. However, it’s essential to manage the SSL proxy feature carefully, as it involves handling sensitive data and it could have an impact on system performance.
A note on SSL Proxy and Next Generation Firewall Performance
SSL Proxy Function can become a significant load on performance for most Next Generation Firewalls. Take as an example two of our top Enterprise NGFW:
| Model | SG-6000-A5600-IN | SG-6000-A5800-IN |
| Firewall Throughput | 60/85 Gbps | 80/95 Gbps |
| NGFW Throughput | 29 Gbps | 32 Gbps |
| Threat Protection Throughput | 18 Gbps | 20 Gbps |
| Maximum Concurrent Sessions | 20 Million | 25 Million |
| New Sessions/s | 800,000 | 930,000 |
| IPS Throughput | 35/60 Gbps | 45/75 Gbps |
| AV Throughput | 20 Gbps | 25 Gbps |
| IPsec VPN Throughput | 36 Gbps | 45 Gbps |
| SSL Proxy Throughput | 8.5 Gbps (10.2 Gbps) | 8.5 Gbps (10.2 Gbps) |
SSL Proxy Throughput is only a fraction of other measurements such as NGFW Throughput or even Threat Protection Throughput. Standard measurement of SSL Proxy Throughput is obtained using AES128-GCM-SHA256 with all IPS rules being turned on. However, in certain scenarios with the right configurations SSL Proxy Throughput can be increased up to 20% using lighter cipher suites, as shown in the above chart. Another factor to take into account when evaluating SSL Proxy Performance is the typical application scenario in which the IPS rules are switched off and the main goal of packet inspection is URL Filtering function.


