MITRE ATT&CK is a great common-knowledge framework to learn and communicate about adversarial behaviors. It can be used to guide threat detection, investigation and response efforts by cybersecurity teams. However, analytics still need be applied to differentiate real threat activities from normal behaviors.
Moreover, correlating threat activities to generate a temporal and spatial attack graph remains a big challenge to the cybersecurity community. In addition, the sheer volume of security alerts – whether true or false – can overwhelm cybersecurity teams and lead to threat alert fatigue.
Behavioral Analytics and Correlation Challenges
Traditional security tools can create TTP (tactics, techniques and procedures) alerts using a static rule set. However, those rules normally have no awareness of the enterprise environment in which they operate. They cannot discern if a behavior is normal or malicious, and thus frequently generate a large number of false alarms.
Behavior analysis tools can use machine learning models to establish a baseline of normal behavior, and detect deviation from the baseline algorithmically. Behavioral analysis can greatly reduce false positives from the baseline, but the burden is still on the security analyst to manually piece together the chain of attack events. If the behavior is truly malicious, the analyst needs to correlate the various stages of the attack across a huge amount of system logs.
A sequence of techniques and tactics used for an attack is what we call a TTP chain. Using typical APT life-cycle specifications, at a high level the attack chain might include initial compromise, privilege escalation, internal reconnaissance, lateral movement, exfiltration and clean-up, etc.
A resolved attack sequence with all the abnormal TTPs put together would give analysts a great edge to tackle behaviors that have a high probability of being true attacks. Several approaches have been tried before, like the kill-chain stage model. The success of those approaches is limited because of the two main issues:
- Lack of causality tracking information. Current tools lack the necessary context to understand the interdependencies between related threat alerts. A timeline of events can help, but the mere order of timed events does not guarantee they have causal relationships. A dependency graph (or provenance graph) is needed to create a system auditing framework, and determine causal dependence between system subjects and objects.
- A semantic gap between low-level system events and a high-level kill-chain view of attacks. To bridge the semantic gap, an intermediate layer is needed to describe behavioral attack patterns. Expert knowledge is required to generate rules to map system-level events to TTP behaviors. It can be a daunting job to create homemade TTP rules.
An Alternative: MITRE ATT&CK
The MITRE ATT&CK framework is a public knowledge base of TTPs. Many top security vendors already use the MITRE ATT&CK framework to describe their threat detections. TTPs from MITRE ATT&CK offer a more pragmatic and representative approach to build a threat correlation model.
The ATT&CK model describes the actions an adversary takes within an enterprise network. The model characterizes adversary behaviors to create common behaviors knowledge across known attack activities. The framework describes individual or combinations of actions that an adversary may take to achieve their goals.
The TTPs described in ATT&CK were selected based on observed APT intrusions from public reporting, and are included in the model at a level of abstraction necessary to effectively understand an attacker’s goals and intentions, and to prioritize defensive strategies.
By using a low-level dependency graph, and mapping threat events to ATT&CK TTPs, we can build TTP chains for enterprise networks and systems. Moreover, the combination of techniques in a TTP chain represents various attack scenarios that can be composed in an attack graph.
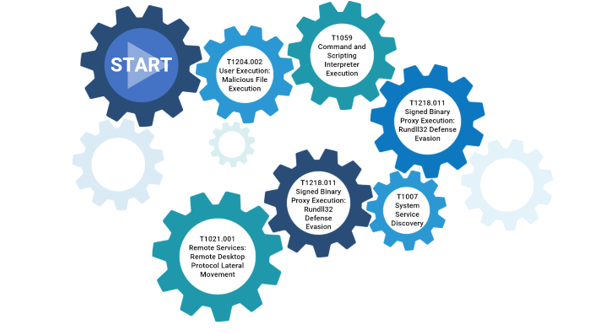
Attack graphs provide compact visualization of multi-stage attacks to analysts, accelerating investigation and response. Just like solving a jigsaw puzzle, when millions of isolated pieces are connected together, the attacker’s intention is revealed, and appropriate actions can be taken to protect the network and its resources.
Conclusion
Legacy enterprise security tools using IOC-based approaches make it difficult for security analysts to fully understand the scope of an attack. Using a TTP-based approach and mapping those events to the ATT&CK framework can help reduce threat alert fatigue and contribute to a stronger security posture.
In addition, ATT&CK can be used to enhance threat detection by adding higher level abstraction for behavioral analytics. ATT&CK is a great framework to communicate and collaborate on threat detection, investigation and incident response. We will have more blogs about various use scenarios of this great knowledge base.



