With everything digital today, various attack methods have emerged, most of which are targeted at the network layer of the TCP/IP stack. Common attack methods include but are not limited to ICMP, ACK, SYN flood and ARP spoofing and flood, among others.
The ARP protocol is the fundamental protocol for the network layer. Once an ARP-Flood attack is launched by an attacker on the access switch of the customer’s network, it has a huge impact on the entire network. Because of this, preventing ARP attacks is super critical.
So, how do you prevent ARP attacks? Let’s go for a deep dive into ARP, how it works, and its vulnerabilities.
What is ARP and how does it work?
In a typical Ethernet based communication, when a Layer 3 IP packet is sent out, it needs to be encapsulated both at the source and destination MAC address ahead of the packet to be a Layer 2 frame. There is a destination IP address in the packet, but where is the destination’s Mac address? Address Resolution Protocol (ARP) is a communication protocol used for discovering the link layer address, such as a MAC address, associated with a given internet layer address, typically an IPv4 address.
For example: Host A, with an IP address 10.0.0.1/24 and MAC address 0000-0000-0001, would like to send a packet to Host B, with IP address 10.0.0.2/25 and MAC address 0000-0000-0002.
However, Host A doesn’t yet know Host B’s MAC address.
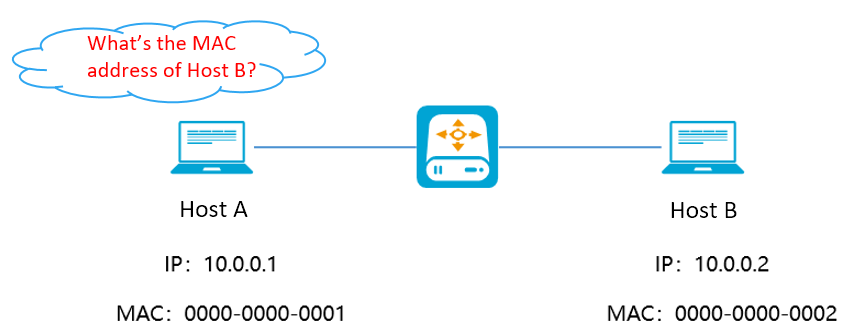
Host A uses ARP to know Host B’s MAC address.
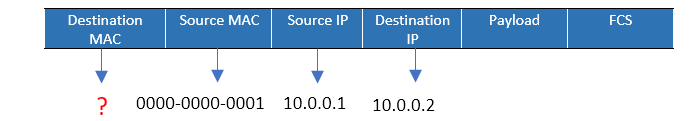
- Host A broadcasts ARP request; destination MAC address is FFFF-FFFF-FFFF
- Host B receives the ARP request, records mapping info for Host A’s IP and MAC address in the local ARP table; replies with ARP response.
- Host A receives the ARP response; records the mapping info of Host B’s IP and MAC address in the local ARP table; encapsulates the IP packet and sends to Host B
Common ARP Attacks
ARP based DOS attacks
- Scenario 1: Since hosts and switches require system resources to resolve ARP packets, attackers use this feature to send out a large number of ARP packets to the target host in an attempt to use up the system resources of the target and make the target host unable to function as normal.
- Scenario 2: After receiving the ARP request message, hosts or switches will record the IP and MAC address of the message, taking up the ARP table entry. The attackers fake a large number of ARP requests of random IP addresses and MAC addresses, resulting in the device unable to process normal ARP requests due to the limited resources of the device.
APR spoofing attacks
Host A would like to communicate with Host B. Host A broadcasts an ARP request. The attacker forges an ARP response by filling its own MAC address as if it were Host B’s. ARP spoofing attacks can allow attackers to intercept or even tamper with data packets to steal data or disrupt network communications.
Hillstone Solution
It is absolutely critical to prevent ARP attacks. The solution? Continuous monitoring and detection of ARP packets.
From a DOS attack perspective: Working in tap mode as a key intranet threat detection device, Hillstone’s sBDS mirrors the traffic from the switch to itself. sBDS’s built-in abnormal behavior detection (ABD) engine continuously monitors ARP packets. If the number of ARP packets reach the threshold of the dynamic detection rule within a specified time period, sBDS generates threat logs and threat event alarms, effectively detecting ARP-based DOS attacks.
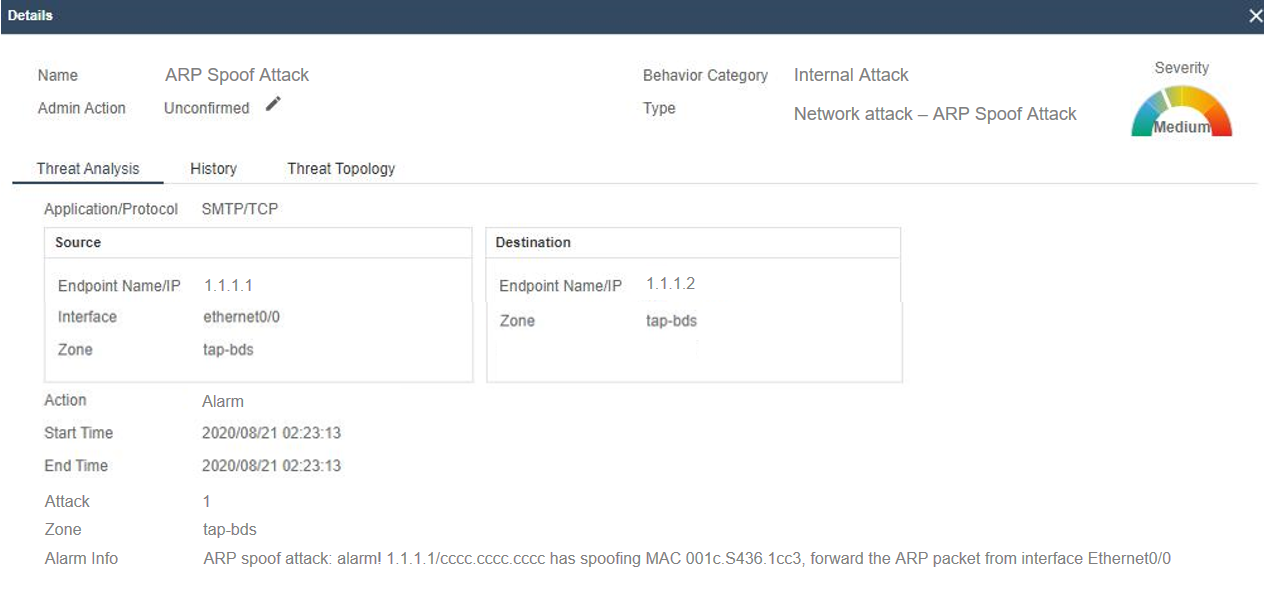
From a spoofing perspective: sBDS compares the IP and MAC address, which is extracted from the network packet, with the IP and MAC addresses in the mapping table entry. If they don’t match, a threat event and threat log will be generated, effectively detecting ARP spoofing. Here is an example of detected ARP spoofing attack event by Hillstone sBDS.
About Hillstone sBDS V3.0
In addition, there are two new sBDS models have been released in addition to the sBDS version 3.0 release. The Hillstone sBDS product portfolio now can cover the full range of user scenarios from 1G to 10G traffic. Highlights of the new release also include:
- Optimized reports: Offers comparisons with past reports, and analysis from various dimensions such as network traffic, risky assets and network threats, as well as user-defined templates.
- Enhancements in the abnormal behavior detection capabilities
- Expanded standard restAPI support, which allows the devices to be managed by 3rd party network management software.
To learn more about Hillstone’s sBDS, please download data sheet, white paper, or schedule an online demo.



