Comprehensive Cloud Protection & Data Security
Hillstone CloudHive Solution
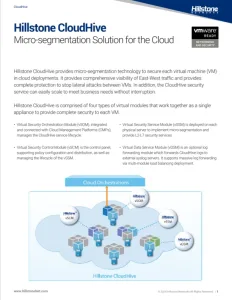
Comprehensive Cloud Infrastructure Protection with Micro-Segmentation
Hillstone CloudHive provides a comprehensive cloud workload protection platform (CWPP) to secure enterprise virtual machines in private clouds. As a robust micro-segmentation solution that integrates seamlessly into both VMware and OpenStack ecosystems, CloudHive provides visibility into East-West data center traffic and provides comprehensive cloud data data security to help block lateral movements that are part of sophisticated multi-stage, multi-layer attacks.
Hillstone CloudHive Value Proposition
Complete Cloud Protection with Unparalleled Visibility
Hillstone’s CloudHive provides enterprises with a complete view of all traffic entering and leaving VMs in any monitored VMs or port group. Insight, which possesses sophisticated visualization tools, allows security and network users to easily spot unusual patterns or use the same data for capacity planning.
Fine-grained Controls for Precise Blocking of Lateral Attacks
With fine-grained controls and application intelligence, CloudHive provides enterprise IT with added peace-of-mind. CloudHive precisely detects and blocks suspicious East-West connections within the data center or between hosts in different data centers. It can even view intra-VM traffic. Application-awareness provides companies with maximum protection while minimizing false positives.
Platform Agnostic Approach for Maximum Flexibility
Drop-in support for VMware and OpenStack allows for the same protection framework everywhere regardless of underlying cloud platform, allowing cloud security teams to create a standardized set of policies and enforcement that spans public and private cloud environments.
Industry-leading performance with better TCO
Blending performance of up to 1Tbps that scales to any size workloads with a flexible CPU-based licensing, CloudHive provides companies with better TCO on a solution that is easily scalable.

Hillstone Networks Recognized in Gartner 2020 Market Guide for Cloud Workload Protection Platforms for its CloudHive Solution

Hillstone CloudHive Resources
Recent Blog Articles
Learn more about Hillstone’s CloudHive data security solutions
Engage with us to learn more or see a demonstration by contacting your local authorized Hillstone Networks reseller.
Contact Us
For the 4th year in a row, Hillstone Networks has been recognized in Gartner Peer Insights Customers’ Choice for Network Firewalls.
The Customers’ Choice is a rating of vendors in a given market — for Hillstone, it’s Network Firewalls — that take into account both the number of reviews and the overall user rating. Based on feedback and ratings from our end users who have purchased, implemented and are happily using our products and services, Hillstone’s overall rating came to 4.9.