IKE VPN Configuration Example
This section describes an example of IKE VPN configuration.
Target: Establishing a tunnel between Device A and B. PC1 is a host behind Device A, with the IP address 10.1.1.1 and gateway 10.1.1.2; Server1 is the server behind Device B, with IP address 192.168.1.1 and gateway 192.168.1.2. The goal of this configuration example is to protect the communication between the subnet of PC1 (10.1.1.0/24) and the subnet of Server1 (192.168.1.0/24), using the method of route-based VPN. Use ESP as the security protocol, 3DES as the encryption algorithm, SHA1 as the hash algorithm and DEFLATE as the compression algorithm.
The topology is shown below:
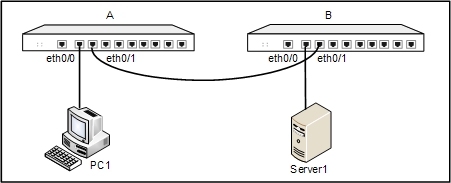
To establish the VPN tunnel, take the following steps:
Step 1: Configure the interfaces of the devices
Device A
- On the Navigation pane, click Configure > Network > Network to visit the Network page.
- Select ethernet0/0 from the interface list, and then click Edit. In the Interface Configuration dialog, configure the options as below:
- Binding zone: Layer 3 zone
- Zone: trust
- Type: Static IP
- IP address: 10.1.1.2
- Netmask: 255.255.255.0
- Click OK to save the settings and return to the Network page.
- Select ethernet0/1 from the interface list, and then click Edit. In the Interface Configuration dialog, configure the options as below:
- Binding zone: Layer 3 zone
- Zone: untrust
- Type: Static IP
- IP address: 1.1.1.1
- Netmask: 255.255.255.0
- Click OK to save the settings.
- Click New on the upper-left of the interface list, and select Tunnel Interface from the drop-down list. In the Interface Configuration dialog, configure the options as below:
- Name: tunnel1
- Binding zone: Layer 3 zone
- Zone: : trust
- Click OK to save the settings.
Device B
- On the Navigation pane, click Configure > Network > Network to visit the Network page.
- Select ethernet0/0 from the interface list, and then click Edit. In the Interface Configuration dialog, modify according to your need:
- Binding zone: Layer 3 zone
- Zone: trust
- Type: : Static IP
- IP address: 192.168.1.2
- Netmask: 255.255.255.0
- Click OK to save the settings.
- Select ethernet0/1 from the interface list, and then click Edit. In the Interface Configuration dialog, modify according to your need:
- Binding zone: Layer 3 zone
- Zone: untrust
- Type: : Static IP
- IP address: 1.1.1.2
- Netmask: 255.255.255.0
- Click OK to save the settings.
- Click New on the upper-left of the interface list, and select Tunnel Interface from the drop-down list. In the Interface Configuration dialog, configure the options as below:
- Name: tunnel1
- Binding zone: Layer 3 zone
- Zone: : trust
- Click OK to save the settings.
Step 2: Configure policy rules
Device A
- On the Navigation pane, click Configure > Security > Policy to visit the Policy page.
- Click New. In the Policy Configuration dialog, configure the options as below:
- Src Zone : trust
- Src address: Any
- Dst zone: : trust
- Dst address: Any
- Service: Any
- Action: Permit
- Click OK to save the settings.
- Click New again. In the Policy Configuration dialog, configure the options as below:
- Src zone: untrust
- Src address: Any
- Dst zone: : trust
- Dst address: Any
- Service: Any
- Action: Permit
- Click OK to save the settings.
Device B
- On the Navigation pane, click Configure > Security > Policy to visit the Policy page.
- Click New. In the Policy Configuration dialog, configure the options as below:
- Src zone : trust
- Src address: Any
- Dst zone: trust
- Dst address: Any
- Service: Any
- Action: Permit
- Click OK to save the settings.
- Click New again. In the Policy Configuration dialog, configure the options as below:
- Src zone: untrust
- Src address: Any
- Dst zone: trust
- Dst address: Any
- Service: Any
- Action: Permit
- Click OK to save the settings.
Step 3: Configure routes
Device A
- On the Navigation pane, click Configure > Network > Routing to visit the Routing page.
- On the Destination Route tab, click New. In the Destination Route Configuration dialog, configure the options as below:
- Destination: 192.168.1.0
- Subnet mask: 255.255.255.0
- Next hop: Interface
- Interface: tunnel1
- Click OK to save the settings.
Device B
- On the Navigation pane, click Configure > Network > Routing to visit the Routing page.
- On the Destination Route tab, click New. In the Destination Route Configuration dialog, configure the options as below:
- Destination: 10.1.1.0
- Subnet mask: 255.255.255.0
- Next hop: Interface
- Interface: tunnel1
- Click OK to save the settings.
Step 4: Configure a P1 proposal
Device A
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page to visit the IPSec VPN page. Click the Phase 1 Proposal tab.
- Click New. In the Phase 1 Proposal Configuration dialog, configure the options as below:
- Proposal name: P1
- Authentication: pre-share
- Hash: SHA-1
- Encryption: 3DES
- DH group: Group2
- Lifetime: 86400
- Click OK to save the settings.
Device B
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page to visit the IPSec VPN page. Click the Phase 1 Proposal tab.
- Click New. In the Phase 1 Proposal Configuration dialog, configure the options as below:
- Proposal name: P1
- Authentication: pre-share
- Hash: SHA-1
- Encryption: 3DES
- DH group: Group2
- Lifetime: 86400
- Click OK to save the settings.
Step 5: Configure an ISAKMP gateway
Device A
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page to visit the IPSec VPN page. Click the VPN Peer List tab.
- Click New. In the Peer Configuration dialog, configure the options as below:
- Peer name: east
- Interface: ethernet0/1
- Mode: Main
- Type: : Static IP
- Peer address: 1.1.1.2
- Proposal 1: p1
- Pre-shared key: hello1
- Click OK to save the settings.
Device B
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page to visit the IPSec VPN page. Click the VPN Peer List tab.
- Click New. In the Peer Configuration dialog, configure the options as below:
- Peer name: east
- Interface: ethernet0/1
- Mode: Main
- Type: : Static IP
- Peer address: 1.1.1.2
- Proposal 1: p1
- Pre-shared key: hello1
- Click OK to save the settings.
Tips: You can also use the following method to configure ISAMP gateway (peer):
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page to visit the IPSec VPN page.
- On the upper-left of IKE VPN List, click New.
- In the IKE VPN Configuration dialog, finish the options of Step 1: Peer using the same parameters as the settings above.
Step 6: Configure a P2 proposal
Device A
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page to visit the IPSec VPN page. Click the Phase 2 Proposal tab.
- Click New. In the Phase 2 Proposal Configuration dialog, configure the options as below:
- Proposal name: P2
- Protocol: ESP
- Hash 1: SHA-1
- Encryption 1: 3DES
- Compression: Deflate
- PFS group: No PFS
- Lifetime: 28800
- Click OK to save the settings.
Device B
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page. Click the Phase 2 Proposal tab.
- Click New. In the Phase 2 Proposal Configuration dialog, configure the options as below:
- Proposal name: P2
- Protocol: ESP
- Hash 1: SHA-1
- Encryption 1: 3DES
- Compression: Deflate
- PFS group: No PFS
- Lifetime: 28800
- Click OK to save the settings.
Step 7: Configure a tunnel named VPN
Device A
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page to visit the IPSec VPN page.
- Click New on the upper-left of the IKE VPN List. In the IKE VPN Configuration dialog, click Import next to Peer name and select east from the drop-down list. Or you can create a new peer (ISAMP gateway).
- Click Step 2: Tunnel to configure VPN tunnel. Configure the options as below:
- Name: VPN
- Mode: tunnel
- P2 proposal: P2
- Proxy ID: Manual
- Local IP/netmask: 10.1.1.0/24
- Remote IP/netmask: 192.168.1.0/24
- Service: Any
- Click OK to save the settings.
Device B
- On the Navigation pane, click Configure > Network > IPSec VPN to visit the IPSec VPN page to visit the IPSec VPN page.
- Click New on the upper-left of the IKE VPN list. In the IKE VPN Configuration dialog, click Import next to Peer name and select east from the drop-down list. Or you can create a new peer (ISAMP gateway).
- Click Step 2: Tunnel to configure VPN tunnel. Configure the options as below:
- Name: VPN
- Mode: tunnel
- P2 proposal: P2
- Proxy ID: Manual
- Local IP/netmask: 192.168.1.0/24
- Remote IP/netmask: 10.1.1.0/24
- Service: Any
- Click OK to save the settings.
Step 8: Bind tunnel to tunnel interface
Device A
- On the Navigation pane, click Configure > Network > Network to visit the Network page.
- Select tunnel1 from the interface list, and click Edit. In the Tunnel binding section of the Interface Configuration dialog, modify according to your need:
- Tunnel type: IPSec
- VPN Name: VPN
- Click Add to add it to the list below.
Device B
- On the Navigation pane, click Configure > Network > Network to visit the Network page.
- From the interface list, select tunnel1 and click Edit. In the Tunnel binding section of the Interface Configuration dialog, modify according to your need:
- Tunnel type: IPSec
- VPN Name: VPN
- Click Add to add it to the list below.
When the settings are completed, the security tunnel between Device A and Device B has been successfully established. The data transmission between the subnet (10.1.1.0/24) and subnet (192.168.1.0/24) is encrypted.

